Warp or Zero Trust: Which Works Best in 2025?
Every organization today faces the challenge of securing users and devices that operate far beyond the traditional office walls. Employees log in from coffee shops, airports, and home networks that are often unsecured. This reality has forced businesses to rethink how they protect sensitive data, applications, and infrastructure.
Cloudflare, a global leader in web performance and security, offers two powerful solutions to address these challenges: Cloudflare WARP and Cloudflare Zero Trust.
Both play critical roles in securing internet traffic and controlling access, but they often raise the question: Warp or Zero Trust, which is better?
To help you choose rightly, this article explains the features, benefits, and differences of both. We analyze how they work individually and together to provide a modern security model. By the end, you’ll understand why choosing between them isn’t always the right approach, and how to leverage both for maximum protection.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: SSO vs Zero Trust: A Complete Analysis for 2025
What Is Cloudflare WARP?
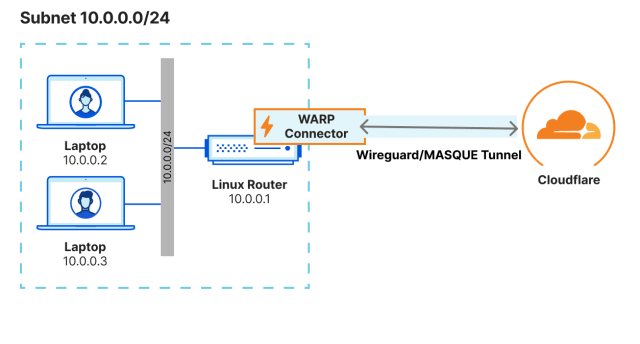
Cloudflare WARP is often described as a VPN, but it’s more accurate to call it a device client that encrypts and optimizes internet traffic. Unlike traditional VPNs that may slow down connections, WARP is designed to make internet browsing faster while protecting users from potential threats.
At its core, WARP works by creating secure tunnels using modern protocols such as WireGuard or MASQUE, along with DNS-over-HTTPS for encrypted DNS queries. These tunnels route traffic through Cloudflare’s massive global network, ensuring that connections remain private and resilient against interception.
The WARP client consists of several key components:
- Graphical User Interface (GUI): The control panel where users can toggle WARP on or off.
- WARP Daemon (or Service): The background engine responsible for building secure tunnels and handling device traffic.
- warp-cli: A command-line tool that allows administrators to configure and manage WARP programmatically.
- warp-diag: A diagnostic tool for troubleshooting, collecting logs, and analyzing connectivity issues.
WARP supports Windows, macOS, Linux, iOS, and Android, making it versatile for organizations with diverse device ecosystems. Once deployed, it enhances privacy by preventing ISPs or malicious actors from snooping on traffic.
For users, the benefits are clear: a lightweight VPN-like solution that improves performance while encrypting data. For organizations, it’s the gateway that brings devices under Cloudflare’s Zero Trust policies.
What is Cloudflare Zero Trust?
While WARP protects individual devices and their traffic, Cloudflare Zero Trust takes security to the organizational level. Zero Trust is a framework built on the principle of “never trust, always verify.” Instead of assuming users or devices inside the network are safe, every request must be authenticated and authorized before access is granted.
Cloudflare Zero Trust provides a cloud-native platform that allows organizations to define, enforce, and monitor security policies from anywhere in the world. It moves away from outdated perimeter-based models and ensures protection even when employees work remotely or connect over untrusted networks.
Key features include:
- Identity-based access controls: Users must authenticate through methods such as SSO, SAML, OIDC, or one-time PINs before gaining entry.
- Device posture checks: Ensures devices meet compliance requirements like OS version, disk encryption, and location before allowing connections.
- Advanced web filtering: Protects against malware, phishing, and unauthorized content with Cloudflare Gateway.
- Secure access to private applications: Cloudflare Tunnels make it possible to connect to internal apps without exposing them directly to the internet.
- Digital Experience Monitoring (DEX): Provides visibility into performance and user activity, enabling proactive issue resolution.
Unlike a traditional VPN, Cloudflare Zero Trust gives administrators granular control over applications, devices, and users. It’s scalable for businesses of all sizes, from startups to large enterprises, offering the same level of protection without complex on-premise hardware.
READ MORE: Perimeter Based Security vs Zero Trust: Which Cybersecurity Model is Better in 2025?
WARP as a Gateway to Zero Trust

It’s easy to think of WARP and Zero Trust as separate options, but in Cloudflare’s ecosystem, they’re deeply connected. WARP acts as the entry point for devices, while Zero Trust provides the rules and policies that govern how those devices interact with corporate applications and data.
When a device connects through WARP, its traffic is routed securely to Cloudflare Gateway, where Zero Trust policies are enforced. This means administrators can apply controls such as:
- Blocking malicious websites with DNS and HTTP filtering.
- Enforcing multi-factor authentication before accessing sensitive apps.
- Checking device posture (e.g., OS updates, encryption, location) before granting access.
- Isolating risky browsing sessions using Cloudflare Browser Isolation.
In other words, WARP is not an alternative to Zero Trust, it’s a foundational piece of it. Without WARP, enforcing consistent Zero Trust policies on remote devices becomes much harder. With WARP, all traffic is funneled into Cloudflare’s secure network, making Zero Trust practical and seamless.
This integration highlights the synergy: WARP provides the secure connection, while Zero Trust defines what can or cannot happen over that connection. Together, they build a security model that is both flexible and future-ready.
Key Differences Between WARP and Zero Trust
Although they work together, Cloudflare WARP and Cloudflare Zero Trust serve different purposes within the security ecosystem. Understanding their distinctions helps organizations know when to use one, the other, or both.
1. Scope
- WARP focuses on securing device traffic by encrypting it and sending it through Cloudflare’s global network.
- Zero Trust provides a comprehensive security framework that governs access to applications, enforces identity verification, and monitors posture checks.
2. Use Cases
- WARP: Best for individuals or organizations that need a fast, secure VPN-like solution to protect browsing and DNS queries.
- Zero Trust: Ideal for businesses that need organization-wide security, including strict control over who accesses what, compliance monitoring, and advanced web filtering.
3. Technology Base
- WARP relies on tunneling technologies like WireGuard and MASQUE, as well as DNS-over-HTTPS.
- Zero Trust relies on identity, access management, and continuous verification of devices and users.
4. Deployment Complexity
- WARP: Quick and simple to install with minimal configuration (Cloudflare WARP download and connect).
- Zero Trust: Requires more setup, integrating identity providers, defining policies, and configuring device posture checks.
5. Value Proposition
- WARP: Enhances privacy, speed, and basic security for users and devices.
- Zero Trust: Offers enterprise-grade protection, preventing lateral movement inside networks and enforcing least-privilege access.
In short, WARP protects the connection, while Zero Trust protects the destination. Organizations often need both working in tandem to achieve holistic security.
SEE ALSO: What Is Zero Trust Architecture in Cybersecurity?
Warp or Zero Trust: Which Is Better?
When people compare Warp or Zero Trust, it’s tempting to frame the choice as either one or the other. In reality, they are not competing technologies but complementary solutions. Each has a distinct role, and the real power comes when they’re used together.
If your focus is individual protection, Cloudflare WARP may be enough. It provides a lightweight, VPN-like service (WARP VPN) that encrypts traffic, prevents data snooping, and enhances browsing speed. For users who want a private connection without the complexity of enterprise tools, WARP alone is a solid option.
However, when organizations need enterprise-wide security, Cloudflare Zero Trust becomes essential. It enforces policies that define who can access applications, under what conditions, and from which devices. It also prevents lateral movement across networks, a major risk in data breaches.
The best approach is not asking Warp or Zero Trust, which is better? But understanding that:
- WARP secures the connection.
- Zero Trust secures the access.
Together, they provide a holistic solution. WARP routes device traffic into Cloudflare’s network, while Zero Trust policies determine whether that traffic should be allowed, blocked, or restricted. For any organization serious about security in the modern workplace, combining both is the winning strategy.
Setting Up Cloudflare WARP and Zero Trust
Deploying Cloudflare WARP and Zero Trust can look complex at first, but the process is structured and straightforward. The goal is to bring every device into Cloudflare’s secure network and apply Zero Trust policies consistently, no matter where users connect from.
Step 1: Create a Cloudflare Zero Trust Account
Visit the Cloudflare Zero Trust website and sign up. The free plan supports up to 10 users, making it perfect for testing before scaling to a paid plan. Once registered, set up your organization’s name and initial configuration in the dashboard.
Step 2: Configure a Login Method
Zero Trust supports multiple authentication methods such as one-time PINs, social logins, SAML, or OIDC. Select and configure the identity provider that aligns with your company’s workflow.
Step 3: Define Device Enrollment Rules
Decide which users can enroll devices into WARP. Rules can be inclusive (allowing specific groups) or exclusive (blocking certain users). Pair these rules with the chosen authentication method.
Step 4: Install the Cloudflare Root Certificate
To ensure encrypted traffic is inspected securely, install the Cloudflare root certificate on all corporate devices. This step is crucial for enabling HTTPS filtering and preventing SSL errors.
Step 5: Download and Deploy the WARP Client
From the Cloudflare Zero Trust dashboard, download the Cloudflare WARP client for Windows, macOS, Linux, iOS, or Android. Install it manually or push it through endpoint management tools. Once installed, users can authenticate with their organizational login.
Step 6: Connect Devices to Zero Trust
After logging in through the WARP client, devices route traffic through Cloudflare’s network. At this point, Zero Trust policies, such as access rules, posture checks, and web filtering, apply automatically.
This process transforms a simple VPN connection into a fully integrated Zero Trust environment, ensuring both privacy and control.
MORE: The 5 Steps to Zero Trust: A Comprehensive Analysis
Benefits of Deploying WARP + Zero Trust Together
When Cloudflare WARP and Cloudflare Zero Trust are deployed together, organizations gain a unified security framework that covers both traffic encryption and access control. This combination brings multiple advantages that go beyond what either solution can achieve alone.
1. Unified Security Policies Everywhere
With WARP funneling traffic into Cloudflare’s network, Zero Trust policies can be applied consistently, whether a user is in the office, at home, or traveling abroad. Security enforcement becomes location-independent.
2. Advanced Threat Protection
Gateway with WARP allows administrators to activate features like:
- Antivirus scanning for malicious downloads.
- DNS and HTTP filtering to block harmful sites.
- Browser Isolation to protect users from risky web sessions.
- Identity-based rules that tie activity to verified users.
3. Device Posture Enforcement
WARP enables Zero Trust to run posture checks on each device. This means access can be restricted if a laptop isn’t encrypted, if the OS is outdated, or if the device is logging in from an unusual location.
4. Secure Private and Infrastructure Access
Through Cloudflare Tunnel, WARP devices can connect securely to internal apps and even infrastructure-level resources like SSH, protected with short-lived certificates and full logging.
5. Better Visibility with Digital Experience Monitoring (DEX)
Admins gain insight into application performance, user behavior, and network health. This allows proactive resolution of issues before they affect business operations.
In short, WARP secures the connection, and Zero Trust secures the destination. Deployed together, they create a comprehensive shield against modern cyber threats, while also improving user experience.
ALSO: What Is Cloud Network Security?
Common Challenges and Considerations
While combining Cloudflare WARP and Zero Trust offers strong security, organizations should be aware of the potential challenges during setup and deployment. Addressing these early ensures smoother adoption.
1. Initial Complexity
Zero Trust requires more configuration compared to a traditional VPN. Identity providers must be integrated, device posture checks defined, and access rules carefully mapped. Without proper planning, this setup can feel overwhelming for smaller teams.
2. User Training and Adoption
Employees may initially view WARP as “just another VPN,” not realizing that Zero Trust adds extra verification layers. Clear communication is essential so users understand why they might face multi-factor authentication prompts or stricter access rules.
3. Compatibility with Existing Tools
Organizations already using identity platforms like Okta or Azure AD must ensure seamless integration with Cloudflare Zero Trust. Most major providers are supported, but misconfigurations can lead to login friction.
4. Free vs. Paid Plans
The free plan supports up to 10 users, which works well for small teams. Larger organizations will need to upgrade to paid tiers, factoring the cost into long-term security budgets.
5. Balancing Security and Productivity
Zero Trust emphasizes security at every step, but if posture checks or policies are too strict, they can slow down workflows. Administrators should fine-tune settings to strike the right balance between safety and usability.
Despite these challenges, the long-term benefits far outweigh the hurdles. With careful rollout and communication, organizations can achieve both strong security and a seamless user experience.
Conclusion
The conversation around Warp or Zero Trust often assumes a choice must be made between the two. In reality, Cloudflare WARP and Cloudflare Zero Trust are designed to work together, not compete. WARP provides the secure, encrypted connection that protects devices and funnels traffic into Cloudflare’s network. Zero Trust applies the policies, verifications, and access controls that safeguard applications and data from unauthorized use.
For individuals, WARP alone delivers privacy and speed, functioning as a fast VPN alternative (WARP VPN). For organizations, Zero Trust ensures that every user and device is continuously verified, minimizing risks that traditional VPNs can’t address. Combined, they create a modern, scalable, and resilient security model that supports today’s remote-first world.
So, when asked Warp or Zero Trust, which is better?, the answer is clear: it’s not about choosing one over the other, but about integrating both for the strongest defense. By deploying WARP with Zero Trust, businesses of any size can achieve consistent protection, improved visibility, and peace of mind in a rapidly evolving threat landscape.
FAQ
Is Cloudflare WARP really faster?
Yes, Cloudflare WARP is often faster than traditional VPNs because it’s optimized to route traffic through Cloudflare’s vast global network. Instead of slowing connections with heavy encryption layers, WARP focuses on efficiency while still encrypting traffic. The result is improved browsing speed, especially when accessing sites and services already optimized by Cloudflare.
Is warp+ a good VPN?
WARP+ is the premium version of Cloudflare WARP that uses Cloudflare’s Argo Smart Routing to accelerate traffic even further. While it’s not a traditional VPN for masking locations or bypassing geo-restrictions, it’s excellent for privacy, security, and speed. WARP+ is especially good for users who want a faster and more stable internet connection compared to the free version of WARP.
Is Cloudflare warp unlimited?
The basic Cloudflare WARP client is unlimited and free to use. However, WARP+, which includes the Argo Smart Routing performance boost, comes with data limitations depending on your subscription plan. So while you can use WARP without limits, WARP+ has caps unless you upgrade for higher usage.
What are the disadvantages of Cloudflare DNS?
While Cloudflare DNS (1.1.1.1) is one of the fastest and most privacy-focused DNS services, there are a few drawbacks:
– It doesn’t include built-in content filtering by default (though this can be added with Cloudflare Family).
– Some websites that rely heavily on geo-based restrictions may not always resolve as expected.
– For enterprise users, Cloudflare DNS requires configuration with other Cloudflare services to unlock full security features, which may be complex for beginners.

