SSO vs Zero Trust: A Complete Analysis for 2025
In cybersecurity, two concepts often dominate conversations: Single Sign-On (SSO) and Zero Trust Security. At face value, they appear to be at odds. SSO simplifies user access by allowing a single login across multiple systems, while Zero Trust strictly enforces verification at every access point, operating under the principle of “never trust, always verify.”
This perceived contradiction raises a critical question for organizations seeking both productivity and protection:
Can SSO vs Zero Trust coexist without compromising security?
As businesses move toward hybrid work, cloud adoption, and a surge in user endpoints, understanding the synergy, or tension, between SSO and Zero Trust is no longer optional. This article explores the differences, clears up the misconceptions, and reveals how SSO, when correctly implemented, can actually strengthen a Zero Trust architecture.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: The Future of SSO – Single Sign-On
What is SSO?
Single Sign-On (SSO) is an authentication method that allows users to log in once and access multiple applications or systems without needing to re-enter their credentials. Instead of juggling dozens of passwords for different platforms, users authenticate through a single trusted identity provider (IdP), which then issues secure tokens to grant access across connected services.
You’ve likely used SSO without even realizing it. When you log in to a new app using your Google, Facebook, or Apple ID, you’re leveraging SSO. It provides a smooth and consistent login experience, especially useful in enterprise settings where employees access many tools daily, email, CRM, HR software, cloud storage, and more.
The benefits of SSO extend beyond convenience. By centralizing authentication, organizations reduce the need for password reuse (a common cybersecurity risk), lower the number of helpdesk requests related to forgotten credentials, and gain tighter visibility into who is accessing what and when. But for all its ease, SSO also introduces a point of concentration: if misconfigured or breached, it could serve as a gateway to all systems.
That’s where Zero Trust comes in, not to replace SSO, but to reinforce it with deeper security controls.
What is Zero Trust?
Zero Trust is not just a security model; it’s a fundamental shift in how organizations think about access and trust. Instead of assuming that users or devices inside the network perimeter are safe, Zero Trust operates on a clear principle: “Never trust, always verify.”
At the heart of Zero Trust is continuous validation. No one, whether internal or external, is granted access by default. Every request must be authenticated, authorized, and evaluated in real-time, using multiple contextual signals like user identity, device health, geolocation, and even behavior patterns.
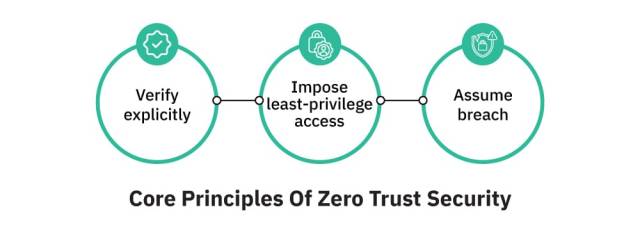
The core principles of Zero Trust include:
- Verify Explicitly: Authenticate and authorize every access attempt using all available data points.
- Use Least Privilege Access: Only grant the minimum level of access required, reducing the potential blast radius of any compromise.
- Assume Breach: Design systems under the assumption that the network has already been infiltrated, thus segmenting and isolating access accordingly.
- Continuous Monitoring: Keep evaluating trust even after access is granted, and revoke it the moment risk increases.
Zero Trust emerged in response to the weaknesses of traditional perimeter-based security, especially as cloud computing, remote work, and bring-your-own-device (BYOD) policies blurred the old boundaries. It redefines the “perimeter” as identity itself, making it the new frontline in cybersecurity defense.
READ MORE: What Is Zero Trust Architecture in Cybersecurity?
The Perceived Conflict: SSO vs Zero Trust
At first glance, SSO and Zero Trust appear incompatible, almost like a tug-of-war between convenience and caution.
SSO is designed to make access easier: log in once, and you’re free to roam across platforms and services without re-authenticating. It minimizes interruptions and streamlines the user experience. On the other hand, Zero Trust is built to make access harder, or rather, smarter. It challenges every connection, regardless of how “trusted” the user or device may appear, to reduce the chance of compromise.
This raises a legitimate concern: If a single SSO login opens the door to everything, doesn’t that contradict the Zero Trust ideal of constantly verifying each access? Critics of SSO within Zero Trust environments often cite the “all-access pass” problem, where compromising one set of credentials could mean breaching every system tied to that login.
However, this perceived conflict is based on a misunderstanding of how modern SSO can be integrated with Zero Trust principles. When implemented poorly, yes, SSO can be a weak link. But when layered with strong identity controls, adaptive authentication, and contextual access policies, SSO becomes not a vulnerability, but a valuable ally in enforcing Zero Trust.
How SSO Supports Zero Trust
While SSO and Zero Trust might seem like opposites, they can actually work together in powerful, complementary ways if SSO is implemented correctly. When layered with robust security protocols, SSO doesn’t weaken Zero Trust; it strengthens it.
Here’s how:
1. Strong Initial Authentication
Modern SSO solutions support multi-factor authentication (MFA) or even passwordless login at the entry point. This aligns perfectly with Zero Trust’s core rule: verify every identity explicitly. The first login becomes a rigorous checkpoint, not a shortcut.
2. Granular Access Controls
SSO isn’t just about access; it’s about who gets access to what. By integrating with Identity and Access Management (IAM) systems, SSO can enforce role-based access, least privilege, and just-in-time permissions. That means users only reach what they’re explicitly authorized to use, which mirrors Zero Trust segmentation.
3. Context-Aware Security
SSO solutions today are not static. They assess risk signals like geolocation, device posture, login time, and behavioral patterns. If a user logs in from a suspicious location or unusual device, access can be blocked or stepped up with additional verification, just as Zero Trust demands.
4. Continuous Monitoring and Revalidation
Zero Trust doesn’t stop at login, and neither should SSO. Integrated with User and Entity Behavior Analytics (UEBA) or Security Information and Event Management (SIEM) tools, SSO can help detect anomalies post-login. If suspicious activity is found, access can be revoked in real time.
5. Centralized Identity Visibility
SSO consolidates access through a single identity provider, giving security teams centralized logs and audit trails. This streamlines monitoring and forensics, both essential for Zero Trust environments.
In short, SSO simplifies the login process, but when fused with real-time analysis, contextual security, and ongoing validation, it becomes a scalable engine for Zero Trust enforcement.
ALSO SEE: Best Zero Trust Microsegmentation Solutions for Cybersecurity in 2025
Real-World Use Cases of SSO + Zero Trust
Theories are great, but real-world implementation is where security models prove their worth. Here are two examples of how organizations are combining SSO and Zero Trust to boost both user experience and security posture.
Use Case 1: A Remote Workforce Secured with Contextual SSO
A global consulting firm transitioned to hybrid work, allowing employees to log in from any location or device. To streamline access, they deployed SSO across all internal apps, from project management to client files. But instead of relying solely on convenience, they layered it with Zero Trust principles.
Every SSO login required multi-factor authentication, and access policies dynamically adjusted based on:
- Device health (e.g., corporate vs. personal laptop)
- Login behavior (e.g., time of day, frequency)
- IP address and geolocation
When an employee attempted to log in from an unrecognized location, the system flagged the session, denied access, and alerted the security team. This prevented a potential phishing breach, all while maintaining a seamless experience for verified users.
Use Case 2: Cloud Access with Role-Based Control
A healthcare SaaS company needed to comply with strict data protection laws (HIPAA). They used SSO to centralize access to electronic health records, admin dashboards, and analytics tools. But with thousands of users, doctors, billing clerks, and customer support, they couldn’t afford blanket access.
So they built access rules tied to user roles and Zero Trust segmentation. Doctors could only see patient data relevant to their department. Support staff could access tickets, but not medical files. All sessions were continuously monitored, and anomalies (like support staff trying to access medical records) triggered automatic lockouts.
MORE: Cybersecurity Salaries: Best 2025 Guide
Best Practices for Aligning SSO with Zero Trust
To truly unlock the synergy between SSO and Zero Trust, implementation must go beyond surface-level integration. Here are the best practices organizations should follow to ensure both convenience and uncompromising security:
1. Enforce Strong, Adaptive Authentication
The entry point of SSO must be fortified. Implement multi-factor authentication (MFA) or even biometric/passwordless methods like FIDO2 keys. Adaptive authentication based on risk, e.g., requiring extra verification from unknown devices or locations, adds a dynamic layer to the login process.
2. Define and Apply Role-Based Access Controls (RBAC)
SSO should not grant blanket access. Use identity and access management (IAM) tools to assign permissions based on job roles, departments, or clearance levels. Tie these roles to your Zero Trust policy to enforce the principle of least privilege across all applications.
3. Integrate SSO with Real-Time Monitoring and Analytics
Pair SSO with tools like UEBA, SIEM, or SOAR platforms that monitor behavior after login. This enables real-time detection of anomalies, like impossible travel (logins from two countries within minutes) or suspicious privilege escalation.
4. Regularly Review Access Logs and User Behavior
Zero Trust is not “set and forget.” Use the audit trails from your SSO provider to periodically review who is accessing what, how often, and whether the access is still justified. Revoke stale access promptly.
5. Conduct Device Posture Checks
SSO should consider device trust as well. Use endpoint detection and response (EDR) tools to assess if the logging-in device has the latest patches, antivirus, encryption, or jailbreak/root detection. Block or sandbox high-risk devices automatically.
6. Apply Conditional Access Policies
Not every login attempt should be treated equally. Set up conditional access rules that respond to risk levels, such as denying access from blacklisted regions, requiring additional verification for high-risk applications, or enforcing stricter rules for contractors.
7. Educate Users on Security Hygiene
Your tech stack is only as strong as the people using it. Train users to recognize phishing, avoid unsafe networks, and report suspicious activity. SSO might streamline access, but Zero Trust demands vigilance from both users and admins.
When these practices are followed, SSO evolves from a login convenience tool into a security powerhouse, one that aligns perfectly with the continuous verification mindset of Zero Trust.
Final Thoughts…
So, is it SSO versus Zero Trust, or SSO with Zero Trust?
The answer is clear: when properly implemented, SSO is not a threat to Zero Trust, it’s a strategic enabler. The frictionless access SSO provides doesn’t have to compromise security. In fact, when paired with the right policies and tools, it enhances it.
The key is not to confuse simplicity with weakness. SSO alone won’t deliver Zero Trust, but SSO plus adaptive authentication, continuous monitoring, and access governance creates a robust security posture that supports both user productivity and enterprise protection.
In a world where cyber threats evolve by the hour and the digital workforce expects ease, it’s no longer a question of choosing between usability and security. The real win is building systems where ease of access fuels secure operations, not bypasses them.
SSO and Zero Trust are not opposing forces. They’re two sides of a modern identity-first security strategy, one that puts context, control, and clarity at the center of every login.
FAQ
Which is better, SSO or MFA?
It’s not about which is better; SSO and MFA serve different but complementary purposes.
SSO (Single Sign-On) simplifies user access by allowing one login across multiple applications.
MFA (Multi-Factor Authentication) enhances security by requiring more than one method to verify identity, like a password and a fingerprint.
The best practice is to combine both: use MFA to secure the initial SSO login, and let SSO handle access across platforms securely.
Is SASE the same as Zero Trust?
No, SASE (Secure Access Service Edge) and Zero Trust are not the same, but they work well together.
SASE is a network architecture that merges wide-area networking (WAN) with network security services (like ZTNA, firewalls, and secure web gateways) into a cloud-delivered model.
Zero Trust, on the other hand, is a security framework focused on never trusting any user or device by default and verifying all access continuously.
Think of SASE as the delivery platform, and Zero Trust as the security philosophy embedded within it.
What are the different types of SSO?
There are several SSO protocols and methods, each with its own use case:
SAML (Security Assertion Markup Language): Often used in enterprise environments for web-based authentication.
OAuth (Open Authorization): Common for mobile apps and websites (e.g., logging in with Google).
OpenID Connect (OIDC): Built on top of OAuth, allowing identity verification in addition to authorization.
Kerberos: Used within Windows-based environments, especially for internal enterprise networks.
Smartcard/Certificate-Based SSO: Often used in government or high-security environments.
Each method serves specific industries and infrastructure types.
What does SSO mean in government?
In a government context, SSO (Single Sign-On) refers to the use of a centralized authentication system to streamline access to internal applications, citizen services, and secure databases.
For example, a government employee may use a single credential to access case management systems, document repositories, and communication tools, while the system logs and verifies every action.
In military or defense sectors, SSO may also refer to a Submarine Safety Officer or Staff Security Officer, but in cybersecurity discussions, it always relates to centralized login solutions.

