What Is Phishing vs Spam: Key Differences, How to Stay Protected in 2026
Your inbox is a battlefield. Every day, millions of deceptive emails compete for your attention, some merely annoying, others downright dangerous. From “limited-time offers” to “urgent account verifications,” these messages might look harmless, but one careless click could expose your private data or empty your bank account.
That’s where the confusion begins: is this spam or phishing?
Both types of emails land in your inbox uninvited, but they serve very different purposes. While spam clutters your inbox with advertisements and promotions, phishing is a calculated attempt to deceive you into giving away confidential information like passwords, banking details, or Social Security numbers.
In this article, we’ll answer the question what is phishing vs spam, how to tell them apart, and why understanding this difference is vital to your online safety. You’ll also learn to recognize real-world examples, the advanced tricks like spoofing and pharming, and the growing rise of “friendly phishing” as a cybersecurity training tool.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: Spear Phishing vs Phishing: Key Differences & 2026 Updates
What Is Spam?
Spam is the digital version of junk mail, unsolicited, irrelevant, and sent in bulk. It’s not necessarily meant to harm you but to grab your attention long enough for someone to make a sale, push a promotion, or advertise a service. These messages often arrive from random or unfamiliar addresses and are blasted out to thousands of people who never asked for them in the first place.
Common examples of spam emails include coupon offers, donation solicitations, fake product discounts, or newsletters you never subscribed to. You might also see random “chain messages,” fake charity drives, or notifications about a contest you never entered. Most of these are commercial, not criminal. Their goal is simple, visibility and sales.
However, spam can still pose risks. Some messages contain links that redirect to shady websites or embed malware-laced attachments disguised as promotional content. That’s why spam filters are now built into nearly every email service. Laws like the CAN-SPAM Act require businesses to include unsubscribe links and honor opt-out requests promptly, reducing the flood of unwanted content.
In essence, spam is unwanted marketing noise, not an immediate cybersecurity threat but a persistent nuisance that can sometimes act as a gateway to more dangerous attacks if ignored.
What Is Phishing?
Phishing is about stealing not selling. Unlike spam, which is merely unsolicited advertising, phishing is a deliberate act of deception designed to trick you into revealing confidential information. It’s one of the most common and dangerous forms of cybercrime because it preys on human trust rather than technical vulnerability.
A phishing attack usually starts with an email or message that appears legitimate. It might look like it’s from your bank, a government agency, or even your employer. The sender may urge you to “verify your account,” “reset your password,” or “confirm a recent payment.” But the link inside often leads to a fraudulent website that mirrors a real one. Once you enter your details, your login, PIN, or card number, the attacker gains access to your private information.
So, what are typical signs of phishing emails?
- A sense of urgency (“Your account will be suspended if you don’t act now”)
- Mismatched URLs (the link text doesn’t match the real website)
- Poor grammar or unusual tone for a known sender
- Requests for sensitive data like passwords or banking details
- Unexpected attachments or forms inside the email
Phishing attacks don’t just target individuals, they also threaten entire organizations. Once a single employee clicks a malicious link, attackers can infiltrate company networks, steal customer data, or install ransomware.
In summary, phishing means manipulating trust to commit fraud. Every element, the logo, the tone, the urgency, is crafted to make you act before you think.
Phishing vs Spam: The Core Difference
Phishing and spam may look similar at first glance; they both show up uninvited, they both use attention-grabbing headlines, and they both ask you to take action. But beneath the surface, their intentions couldn’t be more different.
Spam is primarily about promotion. It floods inboxes with advertisements, offers, and newsletters, hoping you’ll click a link or make a purchase. It’s a digital marketing nuisance, not necessarily a malicious act.
Phishing, however, is about deception. It’s crafted to impersonate trusted sources, banks, government institutions, or employers, to steal your private information. While spam tries to sell you something, phishing tries to take something from you.
Here’s a quick breakdown that captures the distinction clearly:
| Criteria | Spam | Phishing |
| Purpose | Promote products or services | Steal personal or financial information |
| Tone | Informal, promotional, or casual | Urgent, manipulative, or threatening |
| Target Audience | Broad, random recipients | Specific individuals or organizations |
| Level of Risk | Low, mostly annoyance | High, identity theft, financial fraud, malware infection |
| Examples | “Buy 1, Get 1 Free!” or “Join our newsletter” | “Your account is locked, click here to verify” |
To summarize: spam is noise, phishing is a trap.
Spam emails may clutter your inbox, but phishing emails compromise your safety. The ability to recognize these differences is the first step toward protecting your information online.
READ ALSO: Phishing Attack Examples, Types, and Prevention
Spam vs Phishing vs Spoofing
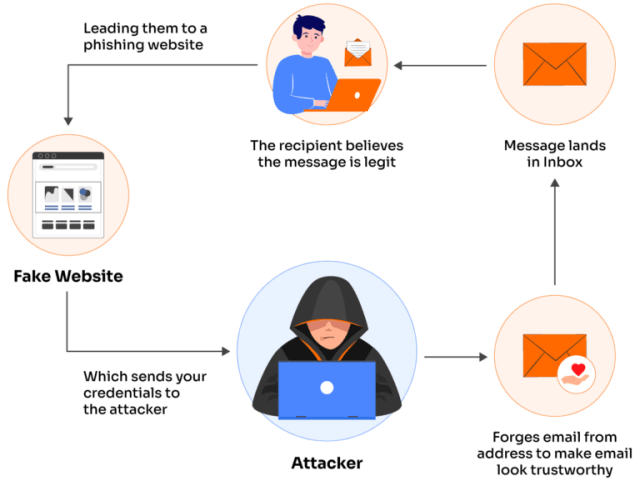
As email attacks have evolved, cybercriminals have found new ways to make their messages look authentic, and that’s where spoofing enters the picture. Spoofing is often mistaken for phishing, but it’s actually a technique that helps phishing succeed.
Spoofing happens when an attacker falsifies the sender’s identity to make a message appear as if it’s from a trusted source. It could look like an email from your bank, your company’s HR department, or a familiar online store. The goal is to gain trust before the victim even reads the content.
For instance, a spoofed message might use a nearly identical domain name such as [email protected] instead of [email protected]. At a glance, it feels legitimate, and that’s all it takes for someone to click without thinking.
This is where spam vs phishing vs spoofing begins to overlap:
- Spam fills your inbox with irrelevant offers.
- Phishing manipulates you into sharing confidential data.
- Spoofing disguises the sender to make phishing harder to detect.
To understand the difference between phishing and spoofing, think of phishing as the scam itself and spoofing as the disguise that makes the scam believable. Spoofing doesn’t always involve stealing information directly, but it often lays the groundwork for phishing and other attacks like malware distribution or ransomware.
In essence, spoofing is the actor behind the mask, creating the illusion of legitimacy so that phishing can deliver the final blow. Together, they form one of the most deceptive combinations in cybersecurity.
Phishing vs Pharming
If phishing is the art of tricking people, pharming is the science of rerouting them.
While phishing deceives users into revealing information through fake emails or websites, pharming quietly manipulates the technical systems behind the internet to redirect users, even when they type the correct web address.
Here’s how it works: Pharming attacks target the Domain Name System (DNS), the internet’s address book. When you type a legitimate website like www.yourbank.com, the DNS translates that into a numerical IP address to take you there. A hacker who has tampered with the DNS can alter that process so that you unknowingly land on a fake version of the site. It might look exactly the same, but every password or card number you enter goes straight into the attacker’s database.
This is the difference between phishing and pharming:
- Phishing relies on social engineering, you’re tricked by a fake message or link.
- Pharming relies on technical manipulation, your traffic is silently redirected.
For example, in a phishing scam, you might get an email claiming to be from your bank asking you to “update your details.” In a pharming attack, you could type your bank’s URL directly and still be taken to a counterfeit site, because the DNS itself has been compromised.
Pharming is particularly dangerous because it removes the need for human error. Even the most cautious users—those who never click suspicious links, can become victims if the attacker controls where their browser lands.
To protect yourself, always check for HTTPS, use secure DNS services, and keep your device software updated. Awareness of both phishing and pharming ensures you’re guarded against deception and technical manipulation.
Types of Phishing Attacks You Should Know
Phishing isn’t one-size-fits-all. Over the years, cybercriminals have refined their techniques, developing multiple forms of phishing attacks designed to exploit different levels of trust and technology. Understanding these types helps you recognize the subtle ways hackers operate—and how to defend yourself before it’s too late.
1. Deceptive Phishing
This is the most common type of phishing attack. Here, the attacker impersonates a legitimate company or service, such as your bank, PayPal, or Amazon, and urges you to click a link or provide sensitive information. Everything from the logo to the tone of the message is crafted to look genuine. For instance, a deceptive phishing email might claim there’s an issue with your payment and ask you to “verify” your details immediately.
2. Spear Phishing
While regular phishing targets the masses, spear phishing is precision-engineered for a specific person or organization. The attacker researches their target, reviewing social media, company websites, or even LinkedIn profiles, to make the email appear credible and personalized. A spear phishing email might include your full name, job title, or details about a recent project, making it far more convincing.
3. Whaling
If spear phishing aims for individuals, whaling targets the “big fish.” These are high-ranking executives, CEOs, or financial officers with access to sensitive systems and data. The emails are sophisticated, often mimicking legal requests or financial transactions. One successful whaling attack can compromise an entire organization.
4. Vishing (Voice Phishing)
Not all phishing happens over email. In vishing, attackers use phone calls or voice messages to impersonate legitimate authorities, like bank officials or government agencies, and pressure victims into revealing private information. A vishing caller might say, “We detected suspicious activity in your account; please confirm your card details to prevent a block.”
5. Smishing (SMS Phishing)
Similar to vishing, smishing occurs through text messages. Attackers send messages claiming you’ve won a prize, missed a delivery, or need to verify your login. Once you click the embedded link, it redirects you to a malicious site that collects your personal data.
Each of these attacks exploits trust in a slightly different way. Whether it’s a carefully crafted email or a convincing voice call, the attacker’s ultimate goal is the same, to get you to act fast without thinking twice.
Friendly Phishing: When Deception Becomes Education
Not all phishing is malicious, some of it is actually friendly. In the cybersecurity world, friendly phishing refers to simulated phishing attacks that companies intentionally send to their own employees as a form of training. The idea is simple: the safest way to learn how to spot a scam is to experience one in a controlled environment.
Here’s how it works. An organization’s IT or security team sends out a fake but realistic phishing email to employees. The email might mimic a delivery notification, a password reset, or even a message from HR. Those who click the link or attempt to enter their credentials are redirected to a secure training page that explains the warning signs they missed.
The purpose isn’t to shame, but to educate. Friendly phishing helps employees recognize the emotional triggers that real hackers use, such as urgency, fear, or reward. Over time, this builds instinctive caution and reduces the company’s overall vulnerability to social engineering attacks.
For example, a friendly phishing campaign might track how many people click on suspicious links and use that data to measure improvement over time. Some organizations even turn it into a game, rewarding teams that detect and report the fake emails fastest.
In essence, friendly phishing turns deception into defense. By safely exposing employees to the same tactics used by criminals, organizations strengthen their first line of defense, their people.
ALSO SEE: MSP vs ITaaS: A Complete 2025 Analysis
Recognizing Red Flags: How to Identify Spam and Phishing Emails
Spotting a suspicious email isn’t always easy, especially when attackers use convincing branding, polished writing, and psychological tricks. Yet, there are consistent patterns and subtle details that can help you distinguish between harmless spam and dangerous phishing attempts. The key is learning what to look for before you click.
Phishing Email Red Flags
Phishing emails are engineered to manipulate emotions and urgency. Here are the most common indicators:
- Urgent or alarming tone: Phrases like “Your account will be suspended in 24 hours” push you to act fast.
- Requests for sensitive information: Legitimate companies never ask for passwords, banking details, or PINs via email.
- Mismatched or shortened URLs: Hover over links to see where they really lead. A URL like paypa1.com instead of paypal.com is a classic warning sign.
- Spelling and grammatical errors: Attackers often operate globally, and even small mistakes can reveal a phishing attempt.
- Unfamiliar attachments or embedded forms: These can install malware or steal credentials once opened.
- Email addresses that don’t match the organization’s domain: For example, a “bank” email coming from a generic Gmail account.
Spam Email Red Flags
Spam, on the other hand, is less targeted but still worth identifying:
- Overly promotional or exaggerated claims like “You’ve won $10,000!”
- Frequent use of emojis, capital letters, or clickbait-style subject lines.
- Random sender addresses or companies you’ve never interacted with.
- Unrequested newsletters or fake charity appeals.
Both phishing and spam exploit human psychology, curiosity, urgency, or greed. But phishing takes it a step further, aiming to compromise security rather than just attention. The more familiar you become with these red flags, the quicker you can detect and report suspicious messages.
Real-World Examples of Spam and Phishing
It’s one thing to know the theory, but recognizing these attacks in real life makes all the difference. Here are a few realistic examples of spam and phishing that show how these threats actually appear in your inbox, and why they’re easy to confuse at first glance.
MORE: Perimeter Based Security vs Zero Trust: Which Cybersecurity Model is Better in 2025?
Example 1: The Promotional Spam Email
Subject: “Congratulations! You’ve Won a Free Trip to Dubai!”
The message includes a bright banner, a “Claim Your Reward” button, and vague text asking you to click to confirm eligibility. It’s loud, promotional, and generic, sent to thousands of recipients at once.
While harmless on the surface, this kind of spam can become risky if the link redirects to a fraudulent website or prompts you to download an attachment.
Example 2: The Payment Alert Phishing Email
Subject: “Payment Issue Detected, Immediate Action Required”
It appears to come from PayPal or your bank, complete with official logos and footers. The email claims your recent transaction was declined and includes a button labeled “Update Billing Info.” Clicking it leads you to a fake login page designed to harvest your credentials. The tone is urgent, the sender seems familiar, and the pressure to act fast can easily cloud judgment.
Example 3: The Fake Invoice Trap
Subject: “Invoice #44512 for Your Recent Purchase”
Phishing emails like this often target professionals. The attached “invoice” may look like a simple PDF but actually contains malware that installs once opened. Attackers use this tactic to breach corporate networks or encrypt data for ransom.
Example 4: The Chain Forward Spam
Subject: “Send This Prayer to 10 Friends and Receive a Blessing”
Though not malicious, these chain messages are classic spam, pointless, repetitive, and spread widely through emotion or curiosity rather than criminal intent.
Each of these examples highlights a truth: phishing hides behind trust, while spam hides behind noise. The more sophisticated the cybercriminal, the more legitimate their message will appear. Recognizing the emotional tone, sender address, and purpose of the email remains the most reliable defense.
How to Protect Yourself from Spam and Phishing Attacks
Awareness is powerful, but prevention is even stronger. While spam and phishing emails are almost impossible to eliminate entirely, you can significantly reduce your risk of falling victim to them by building smarter online habits and strengthening your digital defenses.
1. Use Spam Filters and Security Software
Most modern email services include built-in spam filters that automatically flag or redirect suspicious messages. Keep these filters turned on and updated. Complement them with a reputable antivirus or internet security suite that includes anti-spam and anti-phishing protection.
2. Never Click or Download from Unknown Sources
If an email feels suspicious, even slightly, resist the urge to click links or download attachments. Hover over hyperlinks to preview where they lead. If the URL doesn’t match the sender or looks misspelled, delete the message immediately.
3. Verify Before You Trust
If you receive a message asking for sensitive information, go directly to the organization’s official website instead of clicking through the email. Legitimate institutions will never request personal data through unsolicited messages.
4. Maintain Strong Password Hygiene
Use unique, complex passwords for every account and change them regularly. Consider a password manager to store them securely. Wherever possible, enable multi-factor authentication (MFA) or biometric login for an extra layer of protection.
5. Keep Your Devices and Browsers Updated
Cybercriminals often exploit outdated software to distribute malware. Regularly update your operating system, browsers, and apps to close known vulnerabilities that attackers could target.
6. Report Suspicious Emails
If you’re part of an organization, forward phishing attempts to your IT or cybersecurity team. For personal accounts, mark the message as “Phishing” or “Spam” so email providers can refine their filters and prevent future attacks.
7. Don’t Respond to Spam
Replying, even to unsubscribe, can confirm that your email address is active, leading to even more spam. Instead, block the sender or report the message through your email provider.
8. Back Up Your Data Regularly
Whether through cloud storage or an external hard drive, backups ensure your files remain safe even if an attack succeeds. Ransomware and phishing breaches are easier to recover from when your data is secure elsewhere.
Combining these practices forms a solid digital defense. The goal isn’t to fear every email—it’s to create habits that make you unshakably cautious. When vigilance becomes routine, even the most convincing phishing attempt loses its power.
Conclusion
Phishing and spam may share the same digital space, but their intentions couldn’t be more different. Spam is often a noisy marketing tactic, unwanted yet mostly harmless. Phishing, on the other hand, is a calculated deception built to steal, manipulate, and exploit trust. One fills your inbox; the other can empty your accounts.
In a world where cybercriminals evolve faster than ever, awareness is essential. Every user, from casual emailer to corporate executive, needs to understand that not all emails are what they seem. Recognizing the warning signs, verifying sender identities, and questioning urgency before acting can save you from devastating breaches.
The key takeaway is simple: all phishing emails are scams, but not all scam emails are phishing. Spam may waste your time, but phishing preys on your trust. And in cybersecurity, trust is often the most valuable, and most vulnerable, currency.
By staying informed, using smart protective tools, and adopting vigilant habits, you take control of your digital safety. The internet will always have risks, but with knowledge, discernment, and caution, you can make your inbox, and your data, a much safer place.
FAQ
What happens if I click a phishing link?
Clicking a phishing link can trigger several harmful outcomes depending on the attacker’s intent. The most common is data theft, you might be taken to a fake login page where any details you enter (like usernames, passwords, or credit card numbers) go directly to the hacker.
In other cases, simply clicking the link can download malware onto your device, giving attackers remote access or the ability to steal stored credentials. If you’ve clicked a suspicious link, disconnect from the internet, run a full antivirus scan, and change your passwords immediately.
Why is it called phishing?
The term phishing comes from the idea of “fishing” for victims. Just as anglers use bait to catch fish, cybercriminals use fraudulent emails, texts, or websites as bait to trick users into sharing sensitive information. The “ph” spelling originated in the 1990s, when hackers often used “ph” instead of “f” to sound more technical or underground, a nod to early hacker culture.
Can a VPN protect against phishing?
A VPN (Virtual Private Network) encrypts your internet connection, making it difficult for outsiders to track your online activity or intercept data. However, a VPN cannot stop phishing attacks because phishing relies on social engineering, not network interception.
In other words, a VPN protects your privacy, but not your judgment. You still need to recognize fake emails, suspicious links, and fraudulent websites to stay safe.
What is QR code phishing?
QR code phishing, or “quishing,” is a modern twist on traditional phishing. Instead of sending links in emails, attackers embed malicious URLs inside QR codes. When victims scan these codes with their phones, they’re directed to fake login pages or sites that install malware.
These scams are especially dangerous because QR codes hide the destination URL, making it hard to spot danger until it’s too late. Always verify the source of a QR code before scanning, especially on posters, emails, or text messages from unknown senders.

