What Is a Runbook in Cyber Security? Everything You Need to Know
In cybersecurity, every second counts. When a system goes down or an incident strikes, your team needs more than instincts, they need a documented, proven guide to take immediate action. That’s where runbooks come in.
A runbook in cybersecurity is a step-by-step guide designed to help IT and security teams respond to incidents, maintain systems, and recover from disruptions effectively. It brings clarity, consistency, and speed to operations, especially in high-pressure scenarios.
However, not all response documents are the same. It’s easy to confuse runbooks, playbooks, and SOPs (Standard Operating Procedures), even though each serves a unique function.
This article will break down what is a runbook in cyber security, how it differs from other tools, and how to build one that protects your organization from cyber threats.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED: SQL Injection Vulnerable Sites: Examples, Lists, and Prevention Methods
What Is a Runbook in Cybersecurity?
A runbook in cybersecurity is a detailed, actionable document that outlines the exact steps required to respond to specific security incidents or maintain critical systems. Think of it as a “how-to” manual for IT and security teams, one that removes guesswork during high-stress situations like data breaches, ransomware attacks, or system outages.
Unlike generic procedures, a cybersecurity runbook is tailored to a particular task. For example, if your team needs to isolate a compromised endpoint or restore systems after a DDoS attack, a runbook provides precise instructions to follow, who does what, when, and how. It’s not about theory; it’s about execution.
At its core, a runbook increases speed, accuracy, and consistency. It empowers junior staff to act confidently, reduces the risk of errors, and ensures everyone is on the same page during incidents. In security operations, where minutes matter, this can be the difference between containment and catastrophe.
Types of Runbooks in Cybersecurity

Runbooks aren’t one-size-fits-all, they come in different forms depending on the complexity of the task and the level of automation involved. Understanding the different types helps teams decide what’s best suited for each operational or security need.
1. Manual Runbooks
These are traditional, step-by-step documents executed entirely by human operators. They’re best for tasks that require judgment, oversight, or aren’t yet standardized for automation, like conducting forensic analysis or manually rotating access credentials.
2. Semi-Automated Runbooks
Semi-automated runbooks blend manual steps with scripted automations. For example, an analyst might trigger a script that collects logs while manually reviewing and escalating based on findings. These are ideal for repetitive but sensitive operations that benefit from both precision and flexibility.
3. Fully Automated Runbooks
These runbooks require no human input after initiation. Common for tasks like shutting down infected servers or triggering backup restores, they rely on orchestration tools to execute predefined steps in sequence. They’re especially useful for repetitive or time-critical responses.
4. General Recovery Runbooks
These focus on broad recovery procedures, like restoring infrastructure after a system-wide outage. They often apply across departments and include steps for network restoration, application recovery, and data backup.
5. Incident-Specific Runbooks
Tailored to particular threats such as ransomware, phishing, or insider threats. These runbooks provide detailed protocols for detecting, isolating, and recovering from a specific type of cybersecurity incident.
By maintaining a mix of these runbook types, organizations create a flexible defense system that adapts to both routine maintenance and emergency response needs.
Visit tolumichael.com now to take your first step towards career transformation. Start earning multiple six figures with confidence. Don’t miss out!
Playbook vs Runbook in Cybersecurity
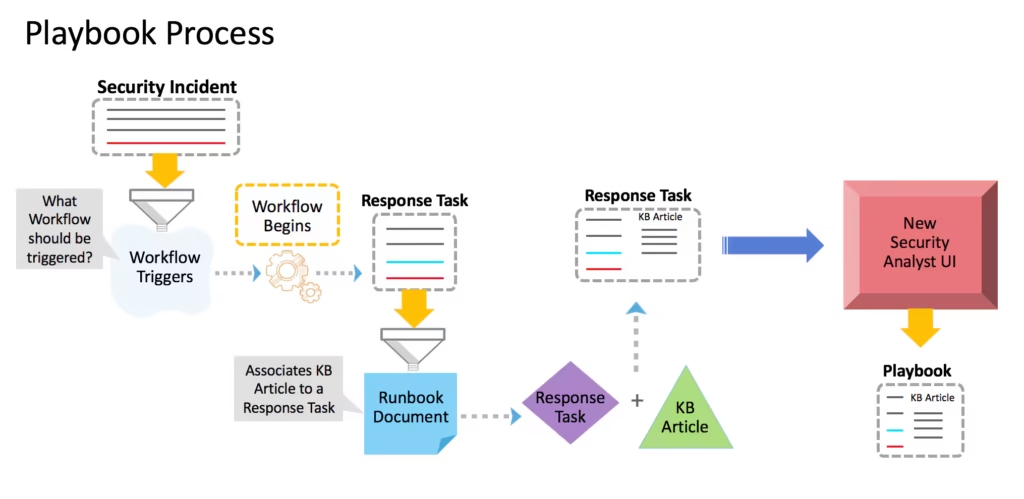
Though often used interchangeably, playbooks and runbooks serve distinctly different roles in cybersecurity operations. Understanding their differences is critical to building a well-coordinated incident response system.
What Is a Cybersecurity Playbook?
A playbook is a high-level strategic guide. It outlines the overall approach to handling an incident, who is responsible, when to escalate, how to communicate, and what frameworks to follow. For example, a ransomware playbook might describe how to coordinate with legal, notify affected users, involve PR, and work with law enforcement.
Playbooks are typically cross-functional and can involve multiple departments like IT, legal, compliance, and customer service. They’re more about decision-making frameworks than technical instructions.
What Is a Cybersecurity Runbook?
A runbook, in contrast, focuses on execution. It provides the step-by-step instructions for the actual tasks, isolating a server, restoring backups, or scanning logs. Runbooks live within the technical scope and are generally carried out by IT or SecOps teams.
Playbook vs Runbook in Cybersecurity: Key Differences
| Feature | Playbook | Runbook |
| Purpose | Strategy & coordination | Task execution |
| Scope | High-level | Detailed/technical |
| Audience | Multi-departmental | Primarily technical teams |
| Format | Narrative, framework | Step-by-step instructions |
| Automation | Rare | Frequently includes automation |
In short, a playbook is the “what” and “why,” while a runbook is the “how.” During a cyber incident, the playbook sets the tone and strategy, and the runbook carries it out.
READ MORE: Is OPNsense a Router or a Firewall? pfSense and OpenWRT
What Is a Runbook in DevOps?

In the world of DevOps, a runbook plays a pivotal role in maintaining speed, reliability, and automation across deployment pipelines and infrastructure operations. It’s not just about cybersecurity, it’s about ensuring uptime, consistency, and rapid response in an always-changing environment.
A DevOps runbook is a documented procedure for operational tasks that are repeatable and essential to system health. These might include restarting services, rolling back failed deployments, provisioning cloud resources, or performing database maintenance. The goal is to codify these tasks so they can be executed with minimal error, even by new team members.
What makes runbooks especially powerful in DevOps is their integration with orchestration tools like Jenkins, Ansible, or Kubernetes. These tools allow parts of the runbook to be automated, reducing manual overhead and improving response time.
By combining clarity with automation, DevOps runbooks help teams:
- Eliminate tribal knowledge silos
- Reduce incidents caused by human error
- Accelerate incident response and recovery
- Ensure every deployment follows best practices
So while runbooks in cybersecurity focus on threat response, runbooks in DevOps focus on operational efficiency and resilience, ensuring systems stay reliable even as they scale.
What Is a Runbook in Project Management?
In project management, a runbook serves a similar purpose to its IT counterpart, standardizing tasks to improve execution but with a broader, cross-functional lens. Here, a runbook is a structured document that outlines repeatable procedures, timelines, roles, and deliverables for a specific phase or recurring process within a project.
Think of it as a project manager’s secret weapon for reducing ambiguity and ensuring that workflows are followed consistently across teams.
Use Cases for Runbooks in Project Management:
- Launching a new product
- Onboarding new clients or employees
- Performing quarterly compliance reviews
- Executing a routine change management process
Each runbook typically includes:
- Objective: What this task or phase aims to achieve
- Owner: Who is responsible
- Steps: Specific actions required, in order
- Dependencies: What must be completed first
- Tools: Any platforms or documents involved
- Timeline: Deadlines or milestones
- Review Process: How success is measured and reviewed
While a playbook in project management outlines general approaches and best practices, a runbook zooms in on execution-level details. And compared to a SOP (Standard Operating Procedure), which governs organization-wide processes, runbooks in this context focus more on project-specific, action-oriented tasks.
In essence, a runbook in project management bridges planning and doing, making sure every member knows exactly what to do when to do it, and how to do it, ensuring that timelines are met and resources aren’t wasted.
Visit tolumichael.com now to take your first step towards career transformation. Start earning multiple six figures with confidence. Don’t miss out!
Runbook vs Playbook vs SOP: What’s the Difference?

It’s easy to confuse runbooks, playbooks, and Standard Operating Procedures (SOPs), especially since they all deal with documenting processes. But, understanding the differences is critical to using each one effectively.
Runbook
A runbook is action-oriented and task-specific. It contains detailed steps for executing a particular process, usually within IT, cybersecurity, DevOps, or project management. Its purpose is to enable fast, consistent execution, especially during incidents or complex workflows.
Example: Restarting a failed server, isolating a ransomware-infected system, or renewing a website SSL certificate.
Playbook
A playbook is strategic and often broader in scope. It defines who does what and when across teams or departments. It offers context, frameworks, and coordination plans during scenarios like crisis response, regulatory compliance, or mergers.
Example: A data breach response playbook that includes legal, public relations, compliance, and IT actions.
SOP (Standard Operating Procedure)
SOPs are formal, organization-wide documents that standardize how recurring processes must be done to meet regulatory, operational, or quality standards. They’re less dynamic than runbooks and are designed to ensure compliance and consistency at a macro level.
Example: An SOP for vendor onboarding that applies across the entire procurement department.
Quick Comparison Table:
| Aspect | Runbook | Playbook | SOP |
| Purpose | Step-by-step task execution | Strategic coordination | Standardization and compliance |
| Scope | Narrow, task-specific | Broad, scenario-based | Department or organization-wide |
| Audience | Technical or project teams | Cross-functional teams | All employees within a process area |
| Flexibility | High | Moderate | Low (often tied to regulation) |
| Examples | Incident recovery steps | Cybersecurity incident response | Quality control procedures, HR processes |
In many real-world scenarios, a playbook may reference multiple runbooks, and SOPs may set the standard that both follow. Each has its place, and when used together, they create a powerful operational ecosystem.
SEE ALSO: Statement of Purpose for Information Security Management
Runbook vs SOP: Which Should You Use?

Choosing between a runbook and a Standard Operating Procedure (SOP) depends largely on the context, purpose, and audience of your documentation.
When to Use a Runbook
Use a runbook when your goal is execution. Runbooks are ideal for:
- Responding to cybersecurity incidents
- Performing regular IT maintenance
- Executing DevOps deployments
- Managing specific, repeatable project tasks
They are dynamic, easily updated, and often customized to reflect the latest best practices or automation workflows. A runbook is especially useful when speed, precision, and task clarity are critical.
Example: If your security team needs to isolate and investigate a compromised endpoint, a runbook will provide the exact commands and tools needed to carry it out quickly.
When to Use an SOP
Use an SOP when your goal is governance or compliance. SOPs are ideal for:
- Meeting industry regulations (e.g., ISO, NIST, HIPAA)
- Standardizing onboarding processes
- Documenting company-wide policies
SOPs are static, formal, and approved by multiple stakeholders. They serve as the official method for completing a process and are often required for audits or certifications.
Example: If your HR department is onboarding a new employee, the SOP ensures every team follows the exact same hiring protocol, regardless of team or location.
How They Work Together
In practice, SOPs and runbooks often coexist. An SOP may require that a specific task be executed “according to the defined runbook,” especially in technical departments. In other words, SOPs define the what, and runbooks handle the how.
Pro tip: If your team is constantly asking, “How do I do this task again?” you need a runbook. If they’re unsure about “What’s the correct way to handle this process?”, you probably need an SOP.
How to Create a Cybersecurity Runbook Template

Building an effective cybersecurity runbook starts with structure. A well-designed template ensures that your team can respond to incidents with clarity, speed, and consistency, especially when under pressure.
Here’s a step-by-step guide to creating a cybersecurity runbook template that works across various threat scenarios:
Step 1: Identify the Use Case
Begin by defining the exact scenario the runbook addresses, e.g., malware containment, ransomware response, or firewall misconfiguration. Be specific. This is not a playbook, it’s task-level documentation.
Step 2: Define the Objective
Clearly state what this runbook is meant to achieve. Examples:
- Isolate an infected endpoint within 10 minutes
- Restore email access after a phishing attack
- Roll back to a clean backup following a ransomware infection
Step 3: List Required Tools and Access
Document any tools, systems, or permissions required to perform the task. This prevents delays and confusion during execution.
Step 4: Write Clear, Step-by-Step Instructions
Break down the task into actionable steps. Use numbered lists, avoid jargon, and include:
- Command lines or screenshots, if necessary
- What to monitor or check at each step
- Expected results and confirmation checkpoints
Step 5: Assign Roles and Responsibilities
Clearly state who does what. This helps avoid bottlenecks and ensures accountability.
Step 6: Include Escalation Paths
If something goes wrong, what’s the next step? Who needs to be informed? Define the escalation policy within the runbook.
Step 7: Add Communication Protocols
Outline how updates will be shared, Slack, email, Zoom, etc. and who needs to be kept in the loop throughout the process.
Step 8: Document Post-Execution Actions
Include steps for documentation, lessons learned, and updating the runbook if needed.
Cybersecurity Runbook Template Outline
Here’s a simplified structure you can reuse:
- Runbook Title
- Objective
- Scenario Description
- Preconditions / Prerequisites
- Tools & Access Required
- Step-by-Step Instructions
- Roles and Responsibilities
- Escalation Procedure
- Communication Channels
- Post-Incident Actions
- Last Reviewed Date / Version Control
Using a consistent runbook template across your team helps improve collaboration, minimize confusion, and boost your organization’s cyber resilience.
MORE: Vanta Vs Tugboat: Everything You Need to Know
Runbook Template and Example
Now that we’ve outlined how to build a cybersecurity runbook, let’s bring it to life with a realistic runbook example using the template shared earlier. This will help you visualize how it all comes together in a practical scenario.
Runbook Example: Ransomware Response
Runbook Title: Ransomware Containment and Recovery – Tier 1 Response
Objective: Contain and recover systems from a ransomware attack without data loss and with minimal downtime.
Scenario Description: Ransomware has been detected on one or more endpoints. Immediate action is needed to isolate, contain, and begin recovery.
Preconditions / Prerequisites:
- Security team has access to EDR (Endpoint Detection & Response) platform
- Admin-level credentials to affected systems
- Verified and recent clean backups
Tools & Access Required:
- CrowdStrike EDR
- Backup and Recovery System (e.g., Veeam, Rubrik)
- Slack/Teams for internal updates
- SIEM dashboard for forensic review
Step-by-Step Instructions:
- Alert Confirmation: Verify ransomware alert via EDR system. Document time and endpoint details.
- Isolate System: Use EDR to remotely disconnect the affected endpoint from the network.
- Assess Scope: Identify any lateral movement via SIEM logs and connected systems.
- Inform SOC Lead: Escalate to Security Operations Center for incident classification.
- Backup Validation: Confirm that a clean backup exists for the affected systems.
- Wipe and Restore: Format the infected system and initiate restoration from the latest clean backup.
- Update and Patch: Ensure all restored systems are fully updated with latest security patches.
- Reintegrate: Reconnect the endpoint to the network after a successful scan.
- Monitor: Keep the system under enhanced monitoring for 48 hours post-recovery.
- Log and Report: Document all actions taken, including timestamps and teams involved.
Roles and Responsibilities:
- SOC Analyst: Confirm alert and isolate system
- IT Admin: Execute wipe and restore
- SOC Lead: Oversee escalation and coordination
- Comms Officer: Draft internal and external statements (if needed)
Escalation Procedure: If the ransomware has spread to critical infrastructure, escalate to CISO and invoke the enterprise-wide disaster recovery plan.
Communication Channels:
- Primary: Slack #Incident-Response
- Backup: Phone tree escalation for out-of-hours
Post-Incident Actions:
- Conduct root cause analysis
- Update EDR detection rules
- Review and update this runbook if gaps were identified
Last Reviewed: March 15, 2025
Version: 1.2
Owner: Cybersecurity Response Lead
This runbook example shows how structure, clarity, and planning come together to support teams during a stressful and fast-moving threat event. It transforms uncertainty into action, making your organization more resilient and responsive.
READ: What Is the Slam Method in Cyber Security?
Best Practices for Maintaining Effective Runbooks
Creating a runbook is just the beginning. To ensure it delivers real value during an incident, it must be kept alive, actively maintained, tested, and improved. A stale runbook is nearly as dangerous as having none at all.
Here are the key best practices for maintaining effective cybersecurity runbooks:
1. Keep It Actionable and Clear
Runbooks should read like instructions, not policy memos. Avoid jargon, lengthy descriptions, or abstract theory. Use plain language, numbered steps, and checklist formatting wherever possible.
Tip: If a junior team member can’t execute it confidently, it needs rewriting.
2. Review and Update Regularly
Cyber threats evolve fast. So do your tools, people, and processes. Schedule quarterly reviews to:
- Remove outdated steps or systems
- Add new tools or integrations
- Reassign roles as team members change
Mark every runbook with a “Last Reviewed” date and version number for traceability.
3. Include Post-Incident Feedback
After every major incident, hold a short post-mortem. Ask: Did the runbook help or slow us down? Then, update it based on lessons learned.
Pro insight: Many improvements come not from theory but from using runbooks under real pressure.
4. Make It Accessible
Runbooks shouldn’t live in obscure folders. Store them in a centralized, searchable repository, like a shared knowledge base, Confluence, or cybersecurity platform like Cutover.
Also, ensure permissions are set so the right people can access them at the right time.
5. Standardize the Format
Every runbook should look and feel the same. This consistency saves time and avoids confusion during incidents. Adopt a standard template across teams, down to naming conventions and step formatting.
6. Automate Where Possible
Use orchestration tools to automate repeatable steps. The more that can be handled by a script, the faster and more error-free your response will be.
7. Train the Team
Don’t assume everyone knows where the runbooks are or how to use them. Host regular drills or walkthroughs, especially for high-impact scenarios. Familiarity builds speed and confidence.
SEE: What Is Reconnaissance in Cyber Security?
Challenges and Best Practices in Creating Cyber Recovery Runbooks
Designing and maintaining cyber recovery runbooks isn’t always smooth sailing. It requires collaboration, foresight, and a clear understanding of both technical details and business impact. If not handled properly, runbooks can end up being bloated, ignored, or simply outdated.
Here are the most common challenges organizations face, alongside proven best practices to overcome them:
Challenge 1: Limited Resources
Problem: Many teams lack the time, staff, or budget to build and maintain detailed runbooks. Documentation often takes a back seat to urgent firefighting.
Best Practice: Prioritize the most critical assets and incidents first. Start small. Focus on high-impact, high-frequency events, then scale out. Use a phased approach.
Challenge 2: Complexity of IT Systems
Problem: Modern IT environments, especially hybrid and cloud-based setups, are complex. Capturing all dependencies, access points, and recovery steps accurately is difficult.
Best Practice: Involve subject matter experts early. Map dependencies visually. Use modular runbooks for components like networking, storage, and applications, and link them under a parent runbook.
Challenge 3: Keeping Pace with Change
Problem: Security tools, team roles, and infrastructure evolve constantly. A runbook created 6 months ago may already be obsolete.
Best Practice: Integrate runbook updates into change management workflows. After system updates or team restructuring, flag associated runbooks for review.
Challenge 4: Low Adherence in Crisis
Problem: During real-world incidents, teams sometimes skip runbooks or improvise—especially under pressure.
Best Practice: Train regularly. Conduct cyber drills and “tabletop exercises” to get teams comfortable following documentation. Make runbooks easy to access and follow under stress.
Challenge 5: Lack of Testing
Problem: Untested runbooks are risky. They might look good on paper but break down when needed most.
Best Practice: Schedule routine simulations. These tests expose gaps, improve confidence, and help align theory with reality. After each test, review and refine.
Challenge 6: Fragmented Documentation
Problem: Some organizations have runbooks scattered across different tools, formats, or even departments, making them hard to locate or trust.
Best Practice: Centralize documentation. Use a dedicated platform or knowledge base with access controls and version history. Ensure every team knows where to find what they need.
Conclusion
In the high-stakes world of cybersecurity, reacting on instinct isn’t enough. You need structure, clarity, and speed, and that’s exactly what a runbook provides.
A well-crafted cybersecurity runbook gives your team step-by-step guidance for responding to threats, recovering from incidents, and maintaining business continuity. It minimizes downtime, reduces human error, and ensures that even under pressure, your team can act with confidence.
But it doesn’t stop there. Runbooks must be tested, updated, and maintained regularly to stay relevant as threats advance. When used alongside playbooks and SOPs, they form a powerful trio where playbooks guide strategy, SOPs define policy, and runbooks drive execution.
Whether you’re working in cybersecurity, DevOps, or project management, having a solid runbook template and clear examples in place ensures your organization is always one step ahead, prepared, resilient, and ready to respond.
FAQ
What is runbooks in cyber security?
A runbook in cybersecurity is a detailed, step-by-step guide that outlines how to respond to specific security incidents or perform routine tasks. It helps teams handle threats like ransomware, phishing, or data breaches with speed and consistency. Runbooks ensure that actions are repeatable, well-documented, and aligned with organizational best practices.
What is a runbook example?
A common runbook example is a ransomware response runbook. It might include steps such as isolating the infected system, notifying the security team, verifying backups, restoring affected data, and logging the incident for review. Each step is clearly assigned and described to enable fast, coordinated action during a crisis.
What is the difference between a runbook and a playbook in cyber security?
A playbook is a high-level strategic guide that outlines how teams should respond to various scenarios (e.g., a data breach), including who to contact and how to communicate. A runbook, on the other hand, provides the exact steps for carrying out technical tasks during that scenario (e.g., restoring systems or revoking access).
Playbook = strategy; Runbook = execution.
What is another name for a runbook?
While “runbook” is the most widely used term, it’s sometimes referred to as an operations manual, incident response procedure, or workflow guide, especially in IT, DevOps, and cybersecurity environments. However, “runbook” remains the most specific and accepted term in technical operations.

