Is a SIEM Agentless? The Complete Guide to Agent vs Agentless Security
Security teams today face huge challenge, managing massive amounts of log data while maintaining full visibility across endpoints, networks, and cloud environments. This is where Security Information and Event Management (SIEM) systems come in.
But one key question always arises during deployment: is a SIEM agentless?
The short answer is that SIEM can operate in agent-based, agentless, or hybrid modes. Each approach determines how data is collected, monitored, and analyzed across your infrastructure. The distinction matters because it affects everything from system performance and scalability to compliance and real-time threat detection.
In this guide, we’ll break down what agentless SIEM really means, how it compares with agent-based setups, and when each method is best suited for your cybersecurity environment. By the end, you’ll understand exactly how to design a SIEM strategy that delivers deep visibility, seamless integration, and maximum security coverage without unnecessary complexity.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: What Is the Difference Between EDR and SIEM?
Is a SIEM Agentless by Design?
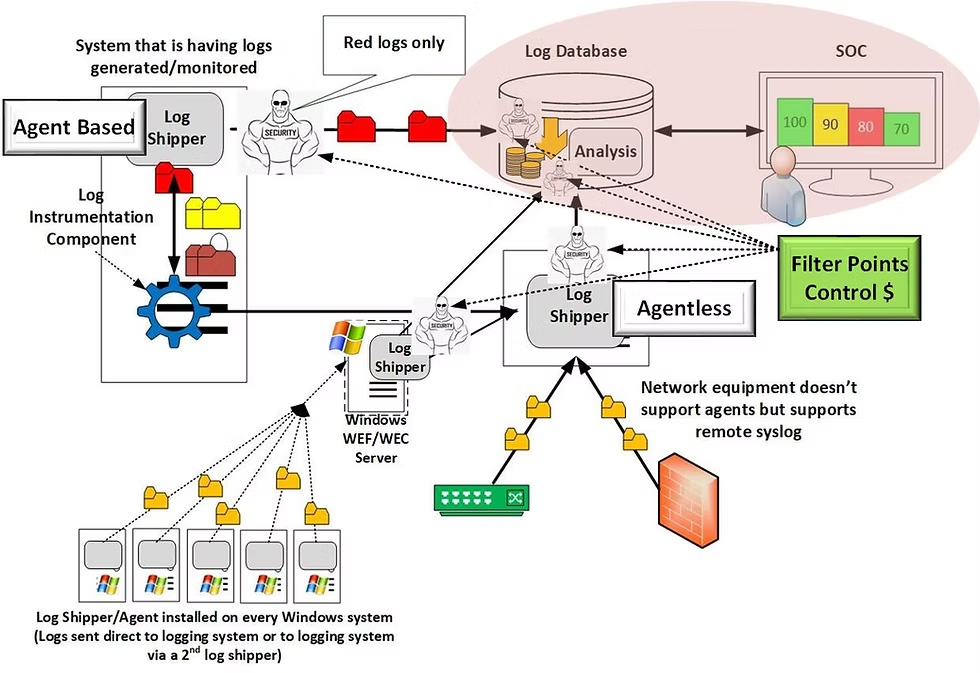
A SIEM can be agentless, but not all are by default. The architecture depends on how it collects and processes log data. In simple terms, agentless SIEMs gather security logs directly from existing systems, such as firewalls, servers, or cloud platforms, through network protocols, APIs, or syslog feeds, without needing to install any software agents on those devices.
However, some SIEM deployments still use agents to collect deeper telemetry data, especially from endpoints that require real-time visibility or granular event tracking.
So, when people ask, “Is a SIEM agentless in cyber security?” the accurate answer is that most modern SIEM solutions are hybrid, they blend agent-based and agentless collection. This ensures broad coverage across all assets while maintaining precision where detailed endpoint monitoring is needed.
In short: yes, a SIEM can be agentless, but the best systems combine both methods for comprehensive security and operational balance.
Understanding How SIEM Works
To understand what makes a SIEM agentless, or not, you first need to know how a SIEM functions at its core.
A Security Information and Event Management (SIEM) system is designed to collect, aggregate, and analyze security data from across an organization’s digital infrastructure. It gathers logs and events from endpoints, firewalls, servers, applications, and cloud platforms, then correlates them to detect patterns or anomalies that may signal security incidents.
At its heart, a SIEM performs several key functions:
- Collection: Gathers raw log data from multiple sources using agents or agentless methods.
- Aggregation: Consolidates logs into a central database for analysis.
- Parsing & Normalization: Converts logs from different devices into a standard, readable format.
- Correlation & Analysis: Detects suspicious behavior by linking related events across systems.
- Alerting & Reporting: Generates notifications and compliance-ready reports based on predefined rules.
The distinction between agent-based and agentless SIEM arises during the collection phase, where the system decides how to gather data, from installed agents on devices or through external network and API connections.
READ MORE: What Is Phishing vs Spam: Key Differences, How to Stay Protected in 2026
What Is Agent-Based SIEM Collection?
Agent-based SIEM collection relies on installing lightweight software agents directly on endpoints, servers, or virtual machines to gather detailed security data. These agents operate continuously in the background, capturing system activities such as process execution, file changes, login attempts, network connections, and user behavior.
Because these agents are embedded within the operating system, they offer deep, real-time visibility into what’s happening on each device. This makes agent-based collection ideal for detecting fileless malware, insider threats, and unauthorized privilege escalation that might not appear in traditional network logs.
The benefits are significant:
- Granular endpoint visibility: Agents capture data that network-only tools can’t.
- Real-time threat detection: Instant alerts and response capabilities.
- Compliance readiness: Meets strict logging standards for frameworks like HIPAA, PCI-DSS, and SOX.
However, this approach comes with trade-offs. Agents consume system resources, require regular updates, and can increase operational overhead, especially in large, diverse environments.
Still, for organizations needing maximum control and precision, agent-based SIEM remains a cornerstone of endpoint-level monitoring.
What Is Agentless SIEM Collection?

Agentless SIEM collection eliminates the need to install any software agents on endpoints or servers. Instead, it gathers data using existing network protocols and integrations, such as Syslog, SNMP, WMI (Windows Management Instrumentation), APIs, and cloud-native connectors. These channels allow the SIEM to collect and analyze logs directly from systems, applications, and cloud platforms without touching the host device itself.
This approach offers speed, simplicity, and scalability. Because there’s no need to deploy agents, organizations can quickly extend visibility across large or diverse environments. It’s particularly useful in:
- Cloud-native or hybrid setups, where APIs provide real-time access to logs.
- Legacy and IoT environments, where devices can’t support additional software.
- Distributed workforces, where managing agent updates can be complex.
The main limitation of agentless SIEM is reduced depth, it can’t capture process-level or user-specific activities occurring within an endpoint. It also depends heavily on network availability; if a device goes offline, visibility drops instantly.
In short, agentless SIEM offers broad coverage with minimal friction, making it ideal for modern, cloud-driven environments that prioritize scale and speed over deep forensic detail.
SEE ALSO: What Does a Cybersecurity Analyst Do? Everything you Need to Know
Agent-Based vs Agentless SIEM: Key Differences
While both agent-based and agentless SIEM solutions aim to collect and analyze security data, they do so in very different ways. Understanding their distinctions is crucial for building a well-balanced cybersecurity architecture.
| Criteria | Agent-Based SIEM | Agentless SIEM |
| Visibility | Deep endpoint visibility — monitors processes, registry changes, user behavior | Broader coverage across networks, cloud, and IoT but with less detail |
| Performance Impact | Can consume system resources (CPU, memory) | Minimal impact since no agents run locally |
| Deployment Speed | Slower — requires manual installation and updates | Faster — setup via APIs, syslog, or connectors |
| Maintenance | High — agents need updates and configuration | Low — fewer moving parts to manage |
| Scalability | Complex in large, diverse environments | Highly scalable across hybrid and cloud systems |
| Cost | Higher (due to installation and maintenance) | Lower (uses existing infrastructure) |
| Best Fit | Regulated industries, real-time detection | Cloud-first or distributed environments |
In essence, agent-based SIEM offers depth, while agentless SIEM provides reach. Most modern organizations combine both, adopting a hybrid SIEM model to balance deep endpoint insight with broad, low-overhead visibility.
When to Use Agentless SIEM
Agentless SIEM is the preferred choice when speed, simplicity, and scalability take priority over granular endpoint visibility. Because it doesn’t rely on installing agents, it can be rolled out rapidly across large, diverse, or cloud-heavy infrastructures, giving organizations immediate visibility into security events without disrupting system performance.
You should consider agentless SIEM in the following situations:
- Cloud-first or hybrid environments: Agentless solutions integrate easily with APIs from AWS CloudTrail, Azure Monitor, or Google Cloud Logging, enabling real-time log collection without installing anything on virtual machines.
- IoT and legacy systems: Devices or older operating systems that can’t support additional software still need monitoring, which agentless SIEM delivers through network-based collection methods.
- Resource-constrained organizations: Small and mid-sized businesses or distributed teams can monitor their environments without dedicating extensive resources to managing agents.
- Fast-moving DevOps pipelines: Continuous deployment environments benefit from the agility of agentless SIEM, which scales automatically with new assets.
In short, agentless SIEM is ideal for organizations seeking quick deployment, wide coverage, and minimal maintenance overhead, especially in dynamic or cloud-driven operations.
When to Use Agent-Based SIEM
Agent-based SIEM is the right choice when deep, real-time visibility and precise endpoint control are essential. Installing agents directly on systems provides unparalleled access to detailed telemetry, allowing security teams to detect, analyze, and respond to threats at the operating system level.
You should deploy agent-based SIEM in these situations:
- High-security industries: Sectors like finance, healthcare, and government demand detailed audit trails to meet compliance frameworks such as HIPAA, PCI-DSS, and SOX. Agent-based collection ensures the required data granularity for regulatory audits.
- Critical infrastructure and real-time detection: Energy, telecommunications, and financial networks rely on instant visibility to prevent operational downtime. Agents can immediately detect and respond to endpoint threats, such as ransomware or insider activity.
- Forensic and investigative needs: When you need to track file modifications, command-line executions, or user session activity, agent-based telemetry delivers the necessary depth.
- Advanced response capabilities: Agents can isolate devices, block malicious processes, and roll back unauthorized changes, actions impossible with agentless setups.
In essence, agent-based SIEM is best suited for environments where compliance, control, and real-time reaction are non-negotiable. It demands more management but rewards teams with unmatched visibility and protection precision.
The Hybrid SIEM Approach: Best of Both Worlds
For most organizations, the smartest choice isn’t purely agent-based or fully agentless, it’s hybrid SIEM. This approach strategically combines both methods, maximizing coverage while minimizing blind spots and operational friction.
In a hybrid SIEM architecture, agents are installed only where deep monitoring is essential, such as on critical servers, databases, and privileged access systems. Meanwhile, agentless integrations handle broader environments like cloud platforms, SaaS applications, and network infrastructure, where installing agents isn’t practical.
This dual setup ensures:
- Comprehensive coverage: Endpoint-level insight from agents + wide visibility through APIs and syslog streams.
- Performance optimization: Fewer agents mean less system load and easier maintenance.
- Scalability: Agentless collection grows automatically with your cloud footprint.
- Unified visibility: All data, whether from agents or network connectors, flows into a single SIEM dashboard for correlation and response.
For example, a healthcare provider might deploy agents on patient data systems for HIPAA compliance while using agentless monitoring for connected medical IoT devices. Similarly, a financial institution can combine both to maintain compliance and detect threats across on-premises and cloud workloads.
Hybrid SIEM delivers the flexibility modern security teams need, depth where it matters and efficiency where it counts.
MORE: MSP vs ITaaS: A Complete 2025 Analysis
Implementation Tips for Any SIEM Setup
Whether you choose an agent-based, agentless, or hybrid SIEM model, success depends on how well you implement and maintain your setup. The quality of your data, the accuracy of your rules, and the efficiency of your response workflows all determine how effectively your SIEM protects your environment.
Here are essential implementation practices to follow:
- Normalize and parse logs properly: Ensure data from different sources is converted into a consistent format. This makes searching, correlation, and analysis far more accurate.
- Use enrichment to add context: Enhance logs with asset details, user identity, and threat intelligence. Context turns raw data into actionable insight.
- Automate correlation rules: Build smart, layered rules that connect multiple events to detect patterns instead of single isolated incidents.
- Optimize indexing and storage: Separate recent logs (hot storage) from archived ones (cold storage) to improve performance and control costs.
- Audit and tune regularly: Review detection rules, agent configurations, and integrations every quarter to eliminate redundancy and improve accuracy.
A well-tuned SIEM is not a “set and forget” system. Continuous optimization ensures your organization stays ahead of evolving threats, without drowning in false positives or alert fatigue.
Conclusion
Choosing between agent-based and agentless SIEM isn’t about picking sides, it’s about aligning your security goals, infrastructure, and compliance needs with the right balance of visibility and efficiency.
An agentless SIEM gives you speed, scalability, and simplified management, perfect for cloud-first or distributed organizations. In contrast, agent-based SIEM delivers granular endpoint data and real-time response capabilities that compliance-heavy industries demand.
The most effective strategy, however, is the hybrid approach. By combining agent-based depth with agentless breadth, you achieve complete visibility without sacrificing performance or agility.
So, is a SIEM agentless? It can be, but the smartest security operations teams use both methods strategically.
If you’re looking to build or optimize your SIEM architecture, start by assessing your data sources and compliance goals. Then, design a hybrid model that scales securely with your business and keeps you ready for tomorrow’s threats.
FAQ
What are agents in SIEM?
Agents in SIEM are small software programs installed on endpoints, servers, or devices to collect log data directly from the operating system. They monitor local activities such as file access, process creation, and login attempts, then forward this information to the SIEM for analysis. Agents enable real-time, granular visibility, something that agentless setups often can’t achieve.
What is agentless cyber security?
Agentless cybersecurity refers to security monitoring and management that does not require installing software agents on endpoints. Instead, it relies on existing infrastructure, like APIs, network protocols (e.g., SNMP, Syslog), or cloud connectors, to collect and analyze data. This approach is faster to deploy, easier to maintain, and ideal for environments where installing software isn’t practical, such as IoT or legacy systems.
Which protocol is commonly used for agentless monitoring?
The Syslog protocol is the most widely used method for agentless monitoring. It allows network devices, servers, and security appliances to send event messages to a centralized SIEM or log management system. Other common protocols include SNMP for device status updates and WMI (Windows Management Instrumentation) for Windows-based systems.
What is the name of the Azure SIEM tool?
Microsoft’s native SIEM solution is called Microsoft Sentinel (formerly known as Azure Sentinel). It’s a cloud-native, agentless-capable platform that uses AI-driven analytics to collect, correlate, and analyze data across hybrid and multi-cloud environments. Sentinel integrates seamlessly with Microsoft Defender and Azure services to deliver unified threat detection and automated response.

