Centralized vs Decentralized Cybersecurity: A Comprehensive Analysis
As organizations scale across regions, adopt hybrid work models, and rely more heavily on digital tools, their attack surfaces grow wider and more complex. Protecting this requires advanced technology and the right cybersecurity architecture, one that aligns with how a business is structured and how it operates.
This is where the debate between centralized vs decentralized cybersecurity comes in. Should your organization maintain full control from a central IT authority, or should it empower departments and regions to manage their own security practices? The answer isn’t always clear-cut.
In this article, we’ll explain both centralized and decentralized approaches, highlight their pros, cons, use cases, and how hybrid approaches are emerging as the preferred strategy for modern enterprises. You’ll also see how these models relate to IT infrastructure, network architecture, access control, and more.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

Centralized vs Decentralized Cybersecurity: Comparison Table
| Aspect | Centralized Cybersecurity | Decentralized Cybersecurity |
| Control Structure | Managed by a central authority (e.g., IT/security team) | Managed by individual departments, regions, or units |
| Decision-Making Speed | Slower for local responses; depends on central approval | Faster, localized decisions and responses |
| Policy Consistency | High uniform policies across the organization | Variables may differ between teams or regions |
| Visibility | Full oversight from a central point | Limited enterprise-wide visibility; siloed monitoring |
| Scalability | Can be a bottleneck as the organization grows | More scalable; units can operate independently |
| Single Point of Failure | Yes — breach or failure at the center can affect all systems | No — compromise is isolated to the affected node/unit |
| Compliance | Easier to enforce and audit regulatory requirements | Harder to standardize compliance without tight coordination |
| Customizability | Low — one-size-fits-all approach to controls | High — can tailor security to specific tools, data, or regulations |
| Best Fit For | Finance, healthcare, government — industries with strict compliance needs | Tech companies, multinational orgs, R&D, manufacturing industries needing local autonomy |
| Examples | HSBC, Bank of America (uniform security enforcement) | Google, Microsoft (divisions like YouTube, Azure, etc., have local control) |
| Access Control Style | Centralized IAM systems control all user permissions | Departments handle their own access policies |
| Implementation Complexity | Easier to deploy and manage uniformly | Complex — requires coordination between units |
| Security Risk Trade-Off | High impact if central systems are compromised | Higher operational risk if policies are inconsistent |
| Hybrid Option? | Can serve as the foundation for a hybrid security model | Complements central controls when designed intentionally |
RELATED ARTICLE: PFSense Central Management: Everything You Need to Know
The Foundations of Cybersecurity Architecture
Before comparing strategies, it’s essential to understand the building blocks of centralized and decentralized cybersecurity, both in theory and in how they operate within an organization.
What is Centralized Cybersecurity?
In a centralized security model, all key cybersecurity decisions and operations are managed by a central authority, typically a dedicated IT or security team at the organization’s headquarters. This team controls policy enforcement, incident response, access management, and system updates across the entire organization.
This approach reflects the essence of centralized access, meaning: a singular control point governs who gets access, how systems are protected, and what protocols are followed. It’s efficient and consistent, ideal for enforcing company-wide compliance and reducing human error.
Benefits of centralized cybersecurity include:
- Uniform policy enforcement across departments and locations
- Easier compliance with regulations like GDPR, HIPAA, or SOX
- Centralized visibility into threats and vulnerabilities
- Streamlined software patching and incident response
However, centralization comes with risks too. If the central system is breached, the entire organization could be compromised. Also, this model may not respond quickly to local threats or context-specific incidents, especially in globally distributed organizations.
What is Decentralized Cybersecurity?
Decentralized cybersecurity shifts the decision-making to multiple units within the organization, such as different departments, regional offices, or business units. Each of these units may operate their own security frameworks tailored to local threats, technologies, and regulatory environments.
This model thrives in industries that value agility and responsiveness, like technology, manufacturing, or retail chains with geographically dispersed operations.
Key advantages include:
- Faster local response to incidents
- Custom security solutions that reflect regional risks
- Resilience against single points of failure
- Greater autonomy and innovation at the edge
However, decentralization can also introduce policy fragmentation, inconsistent standards, and difficulty in oversight. Without coordination, different teams may duplicate efforts or leave vulnerabilities open.
SEE ALSO: How to Check If Port 25 Is Open?
Centralized IT vs Decentralized IT: The Broader Infrastructure Context

Cybersecurity strategies don’t exist in a vacuum; they’re deeply intertwined with an organization’s overall IT architecture. Whether your organization runs on centralized IT or decentralized IT systems will heavily influence how cybersecurity is planned, executed, and maintained.
1. Centralized IT
In a centralized IT environment, all technology infrastructure, servers, databases, user management, security tools, is controlled from a core hub. IT resources are shared across departments, and changes are rolled out uniformly. This structure supports a centralized security model where oversight is tighter, processes are standardized, and compliance is easier to enforce.
From a cybersecurity perspective, centralized IT enables:
- Global visibility across the entire tech stack
- Easier rollout of threat detection tools and updates
- Uniform enforcement of firewalls, antivirus, and endpoint protection
- Predictable access control protocols
Yet, the flip side is vulnerability to systemic failure. If the centralized IT system is attacked or misconfigured, it can affect the entire business ecosystem, an issue that’s especially risky in high-volume or always-on sectors.
Decentralized IT
Decentralized IT structures allow business units or regions to manage their own infrastructure. For example, a company with offices in five countries might allow each location to manage its own local servers, help desk, and cybersecurity policies. This design supports decentralized cybersecurity, allowing each unit to react faster and tailor security based on its unique exposure.
Security-wise, decentralized IT empowers:
- Local control over software, access permissions, and configurations
- Faster patching and response to region-specific threats
- Improved resilience: if one office is compromised, others remain unaffected
However, decentralization can cause misalignment between IT teams. Without clear standards or communication channels, security gaps can emerge. Some departments might run outdated software or use weak authentication systems simply due to oversight or autonomy.
This infrastructure layer, how IT is structured, directly shapes how network security and access control function across an organization.
READ MORE: RTU vs PLC: Key Differences, Use Cases, and How to Choose the Right System
Centralized vs Decentralized Network Security: Key Differences
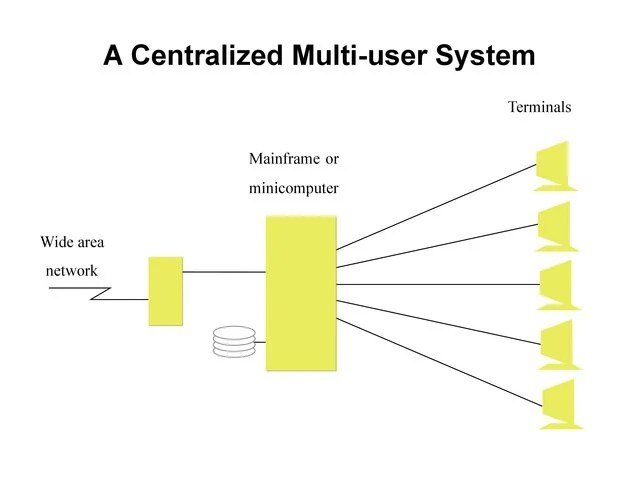
When it comes to safeguarding an enterprise’s digital environment, how a network is structured plays a critical role. Centralized vs decentralized network security refers to the architecture used to enforce controls, monitor activity, and defend against threats across an organization’s endpoints and systems.
Centralized Network Security
A centralized network connects all systems and devices to a single or closely clustered set of servers. Security is managed at the core, with firewalls, intrusion detection systems (IDS), access controls, and logs all running through this central hub.
This setup allows security teams to:
- Monitor all activity from one dashboard
- Standardize firewall rules and VPN access
- Apply patches and updates quickly across the network
- Detect threats early through centralized analytics
The downside? If the central network is breached or goes offline, everything connected to it is affected. Latency issues may also arise, especially for global enterprises whose remote offices rely on routing traffic through the central hub.
Decentralized Network Security
In a decentralized network, each department, office, or location can manage its own security perimeter. Firewalls, antivirus tools, and access policies are locally maintained, and traffic doesn’t need to route through a single central server.
This approach provides:
- Faster, location-specific decision-making
- Greater flexibility in responding to regional regulations or threats
- Local optimization for performance and resource usage
However, decentralization makes coordination more complex. For instance, detecting a coordinated attack across locations may be delayed if each unit monitors threats independently. Furthermore, inconsistencies in tools or policies can increase exposure to cyberattacks.
The network structure you choose sets the ground rules for access control, which is where we’ll turn next, diving deeper into how organizations decide who can access what, and how.
ALSO: What Is Zero Trust Architecture in Cybersecurity?
Centralized vs Decentralized Access Control: Who Gets In and How?

Controlling access to systems, data, and applications is one of the most important pillars of cybersecurity. How access is managed, centrally or locally, can determine how well an organization can prevent internal breaches, detect anomalies, and enforce compliance.
Centralized Access Control
In a centralized access model, permissions are governed from a single authority, often an identity and access management (IAM) system overseen by a core IT or security team. All user credentials, role-based permissions, and access logs are managed in one place.
Centralized access meaning includes:
- A master system that determines who can log in, where, and under what conditions
- Standardized user provisioning and de-provisioning
- Easier auditing, especially for compliance-driven industries like finance or healthcare
This method offers consistency and clear oversight. For example, if an employee leaves the company, HR and IT can disable access across all tools in minutes. However, if the centralized system fails or is compromised, attackers may gain sweeping access to the organization’s assets.
Decentralized Access Control
Decentralized access control gives individual departments or regions the ability to manage their own permissions. Rather than relying on a global IAM platform, local administrators define access rules based on contextual needs.
Decentralized access control examples include:
- A manufacturing plant segmenting operational technology (OT) access separately from corporate IT
- A regional office in Europe assigning data privacy roles in alignment with GDPR
- A software engineering team granting elevated access for DevOps tools not available to the sales team
This model increases agility and responsiveness but can lead to fragmentation. If access revocation isn’t synchronized, former employees or contractors might retain entry into sensitive systems. It also complicates centralized visibility, making it harder to spot risky behavior across the entire organization.
Both models offer benefits, but as networks grow and compliance standards tighten, organizations often look for a balanced, hybrid approach to access control.
MORE: What Is the Difference Between EDR and SIEM?
Real-World Use Cases: Centralized vs Decentralized Security Examples

To understand how centralized and decentralized cybersecurity strategies play out in the real world, it’s helpful to look at how different industries implement them, based on regulatory demands, operational needs, and organizational size.
Centralized Security Example: Financial Institutions
Take global banks like HSBC or Bank of America, they operate in highly regulated environments and must comply with strict standards like PCI DSS, GLBA, and SOX. To ensure uniformity and compliance, these institutions typically adopt a centralized security model.
All network activity, access control, data encryption, and incident response processes are managed by a core cybersecurity team. This central command structure allows for:
- Immediate policy updates across all global branches
- Unified incident response strategies
- Centralized threat detection using SIEM platforms
- Simpler regulatory audits and reporting
For these institutions, centralized IT and security are not just efficient, they’re necessary for legal and operational survival.
Decentralized Security Example: Tech Companies
Contrast that with companies like Google or Microsoft, which operate numerous independent business units, such as Google Cloud, YouTube, or Azure.
Each of these divisions handles different types of data and faces unique security challenges. Google Cloud, for instance, requires robust encryption and container security, while YouTube deals with real-time content moderation and user-generated content threats.
As such, Google uses a decentralized cybersecurity model where:
- Each division manages its own policies and access controls
- Localized incident response teams address unique risks
- Security innovations are fast tested and deployed by autonomous teams
This agility allows Google to adapt fast, but it also requires strong internal communication to avoid gaps or inconsistencies.
These centralized vs decentralized security examples demonstrate that the “right” approach often depends on your business model, threat profile, and the pace at which your organization operates.
READ: LLM AI Cybersecurity & Governance Checklist: A Practical Guide
Hybrid Security Models: Combining the Best of Both Worlds

Today, most modern enterprises are no longer asking “Should we centralize or decentralize security?” Instead, they’re asking, “How do we blend both models to fit our unique needs?” Enter the hybrid security model.
A hybrid approach integrates the control and visibility of centralization with the speed and adaptability of decentralization. It’s not just a compromise, it’s a strategic alignment that supports business growth, compliance, and operational efficiency.
How It Works:
- Centralized Governance: Core policies, identity management, and compliance enforcement remain under central IT authority. This ensures consistency, auditing, and a unified security posture.
- Decentralized Execution: Local departments or regions implement security controls that reflect their specific needs, such as endpoint configurations, local access settings, or data residency requirements.
This model allows for centralized access control at the enterprise level, while also enabling decentralized access control examples in remote offices or specialized teams.
Why Enterprises Are Moving Toward Hybrid Models:
- Global Reach, Local Risk: Enterprises with global networks need to comply with varying data laws while defending against region-specific threats.
- Business Agility: Hybrid models reduce bottlenecks by giving teams localized decision-making power without compromising enterprise-wide visibility.
- Resilience: If the central system is disrupted, local units can continue to operate with minimal impact.
Managed Service Providers (MSPs) often support hybrid implementations, offering centralized tools like SIEM or EDR while allowing for local customization and integrations.
That said, managing a hybrid setup requires strategic planning. Without clear governance, organizations risk creating silos, duplicating efforts, or misaligning security objectives. But when done right, hybrid models can offer the visibility of a centralized security model with the resilience and responsiveness of decentralized cybersecurity.
Strategic Considerations: Choosing the Right Model for Your Organization
There’s no universal blueprint for cybersecurity architecture. Whether you opt for a centralized, decentralized, or hybrid model depends on your organization’s structure, industry requirements, and risk profile. Making the right choice requires a clear-eyed assessment of both internal operations and external pressures.
1. Organizational Size and Complexity
Larger enterprises with multiple departments or global operations often benefit from a centralized security model for consistency and compliance. Smaller or fast-moving companies may prefer decentralized cybersecurity to stay agile and adapt quickly to change.
2. Regulatory Environment
Heavily regulated sectors, finance, healthcare, and government, tend to favor centralization due to the need for standardized policy enforcement and clear audit trails. Meanwhile, industries with fewer compliance constraints (like media or tech startups) can thrive with more decentralized control.
3. Risk Tolerance
Organizations with low risk tolerance often centralize security to minimize potential exposure. High-growth or innovation-driven businesses might accept more risk in favor of speed and local autonomy, leaning toward decentralized structures.
4. Talent and Resource Availability
A shortage of cybersecurity talent can push organizations toward centralized IT, where fewer people manage more systems from one point. On the flip side, if an organization has strong local teams or partners, it may support a decentralized or hybrid model more effectively.
5. Business Culture
A command-and-control corporate culture typically aligns with centralization, while decentralized models work better in collaborative or entrepreneurial environments where teams are empowered to make quick decisions.
6. Digital Maturity
Mature organizations often build hybrid models, centralizing governance while decentralizing tools and execution. Less mature businesses may need to start with a simple centralized structure before layering in complexity.
The decision is less about choosing sides and more about matching your cybersecurity governance to your operational reality. The key is clarity: define who controls what, where, and why.
SEE: Best Branch Network Service for Enhanced Security in 2025
Governance Development in a Distributed World
The future of cybersecurity governance will not be decided by a binary choice between centralized and decentralized; it will be driven by the realities of distributed systems, global threats, and the increasing complexity of digital ecosystems.
Here are the key trends shaping the next era of cybersecurity architecture:
1. Distributed Work and Infrastructure
The rise of hybrid work environments means employees now access sensitive systems from homes, co-working spaces, and mobile devices across continents. This calls for decentralized access control mechanisms that can flex with context, location, device, role, while still being governed by centralized policies.
2. Cloud and Edge Computing
As businesses shift toward cloud platforms and edge computing, centralized IT vs decentralized IT becomes even more blurred. Workloads no longer sit in a single data center, they’re distributed across regions and providers. Cybersecurity strategies must now account for distributed control, latency, and data residency laws.
3. AI-Powered Threat Detection
Artificial intelligence is enhancing both centralized and decentralized systems. In a centralized security model, AI supports unified threat detection and faster incident response. In decentralized setups, AI enables edge devices or local units to independently detect and respond to anomalies in real time, without waiting for central approval.
4. Emerging Regulations
Global data privacy laws like GDPR, CCPA, and the upcoming EU Digital Operational Resilience Act (DORA) are pushing enterprises to rethink governance. Organizations may centralize data management for compliance, but decentralize execution to meet regional legal nuances.
5. Zero Trust and Adaptive Access
The Zero Trust model, “never trust, always verify”, is becoming the default. This philosophy blends centralized identity verification with decentralized enforcement. Access decisions are made based on real-time risk assessments, device posture, and behavioral patterns, not just static rules.
6. Automation and Orchestration
Security orchestration tools now allow businesses to automate processes across both centralized and decentralized systems. Whether it’s provisioning access, updating firewall rules, or managing incident response, orchestration brings unity to complex, distributed environments.
Looking ahead, successful cybersecurity strategies will be defined not by rigid architectures but by how adaptable they are to change, whether that means scaling globally, absorbing new technologies, or navigating unanticipated risks.
Conclusion
The debate between centralized vs decentralized cybersecurity is about understanding your organization’s architecture, risks, and strategic priorities, and then designing a cybersecurity model that fits.
A centralized security model brings consistency, clarity, and compliance, especially useful in regulated industries or large-scale organizations. On the other hand, decentralized cybersecurity enables speed, flexibility, and resilience, key traits for fast-moving teams, global branches, or complex tech environments.
As businesses adopt distributed systems, shift to hybrid work models, and face increasingly sophisticated cyber threats, the future lies in smart hybrid models, those that blend the centralized governance of IT with decentralized execution on the ground.
Cybersecurity isn’t just a technical decision; it’s a business one. And the right model isn’t just the one with the best tools, but the one that aligns with how your organization thinks, grows, and responds to change.
FAQ
Which is more secure, centralized or decentralized?
Neither model is inherently more secure; it depends on the context. A centralized system offers tighter control, consistent policy enforcement, and easier compliance monitoring. However, it also creates a single point of failure; if the central system is breached, the entire organization can be compromised.
In contrast, a decentralized system increases resilience by distributing control and limiting damage from localized attacks. It also adapts well to local threats and operational diversity, but may suffer from inconsistent policies and coordination gaps.
For most modern organizations, a hybrid approach is the most secure, combining centralized oversight with decentralized execution for balanced protection.
What are the 4 types of decentralization?
The four commonly recognized types of decentralization are:
1. Political Decentralization
Transfer of decision-making power from central governments to local or regional authorities.
2. Administrative Decentralization
Redistribution of authority and responsibility for public services across different levels of government or departments.
3. Fiscal Decentralization
Local governments or units gain authority over budgeting, taxing, or spending, allowing financial independence.
4. Market or Economic Decentralization
Power is given to private entities, organizations, or networks, such as in blockchain or decentralized cybersecurity systems, rather than being held centrally.
What is decentralization also called?
Decentralization is also referred to as:
– Distributed governance (especially in cybersecurity and IT)
– Delegated control
– Devolved authority (commonly used in governance and policy contexts)
– In the blockchain world, it’s also known as peer-to-peer (P2P) architecture or distributed ledger technology (DLT).
These terms all refer to systems where decision-making and control are spread out, rather than concentrated in a central body.
How would a decentralized internet work?
A decentralized internet, often called Web3 or the distributed web, would remove control from a few large centralized entities and distribute it across many independent nodes.
Instead of relying on centralized servers (like Google or Facebook), a decentralized internet would:
– Use peer-to-peer protocols to share data directly between users
– Store content on blockchain or distributed file systems like IPFS (InterPlanetary File System)
– Allow users to own their identities, data, and digital assets
– Enhance privacy and censorship resistance by minimizing control from governments or corporations.
In short, a decentralized internet would shift power from centralized platforms to the individuals who use and build the web.

