Best Zero Trust Microsegmentation Solutions for Cybersecurity in 2025
In 2025, traditional security methods, like firewalls and antivirus software, are no longer sufficient to protect organizations from advanced cyber threats. As cyberattacks become more rampant, businesses are turning to more robust security strategies, and one of the most effective approaches is Zero Trust.
Zero Trust security models operate under the principle of “never trust, always verify,” ensuring that no user or device, inside or outside the network, is trusted by default. This approach is particularly effective in combating modern threats where attackers often bypass perimeter defenses. Microsegmentation plays a key role in implementing Zero Trust by segmenting networks into smaller, isolated zones, minimizing the potential damage from a breach.
In this article, we will analyze the best zero trust microsegmentation solutions for cybersecurity and take a closer look at top microsegmentation vendors such as Illumio, Akamai, and VMware. We’ll also discuss how these solutions help businesses build a stronger security posture and why they are essential in today’s cybersecurity space.
If you’re ready to take the next step in your tech career journey, cybersecurity is the simplest and high-paying field to start from. Apart from earning 6-figures from the comfort of your home, you don’t need to have a degree or IT background. Schedule a one-on-one consultation session with our expert cybersecurity coach, Tolulope Michael TODAY! Join over 1000 students in sharing your success stories.

RELATED ARTICLE: The 5 Steps to Zero Trust: A Comprehensive Analysis
What is Zero Trust Security?
Zero Trust security is a cybersecurity framework that operates on the premise that no user, device, or system should be trusted by default, regardless of whether they are inside or outside the network perimeter. Instead, every user and device must be continuously verified before accessing any resource within the network.
This approach challenges the traditional “trust but verify” model, where internal users were inherently trusted once inside the network. In contrast, Zero Trust enforces strict access controls, including multi-factor authentication (MFA), continuous monitoring, and the principle of least privilege access, to mitigate the risk of both internal and external threats.
What is Microsegmentation?
Microsegmentation is a security technique that divides a network into smaller, isolated segments or “zones.” Each segment has its own security policies, ensuring that only authorized traffic can pass between them. This contrasts with traditional network segmentation, which typically divides networks into broad zones (e.g., guest Wi-Fi vs. corporate intranet).
Microsegmentation works at a much more granular level, isolating specific workloads, applications, or even individual devices.
By isolating segments within the network, microsegmentation prevents attackers from moving laterally across the network once they gain access to one segment. If a breach occurs in one segment, the rest of the network remains protected, minimizing the potential damage.
The Relationship Between Zero Trust and Microsegmentation

Microsegmentation plays a crucial role in the Zero Trust model by offering a deeper level of network security. While Zero Trust verifies each user and device, microsegmentation isolates critical resources and workloads within the network, ensuring that even if an attacker bypasses initial security checks, they cannot move freely throughout the system.
For example, in a Zero Trust network, a device might be granted access to one segment of the network but not another, especially if the device is deemed untrusted or compromised. By combining microsegmentation with Zero Trust, organizations ensure a comprehensive approach to network security that limits potential attack surfaces.
READ MORE: Top 10 GRC Tutors in USA for Tech/Cybersecurity Beginners
Key Benefits of Microsegmentation in Zero Trust
Microsegmentation is a vital part of any comprehensive Zero Trust strategy, providing enhanced security, compliance, and operational efficiency. Let’s break down the core benefits of integrating microsegmentation with Zero Trust security.
- Improved Security Posture
One of the primary advantages of microsegmentation is its ability to improve an organization’s overall security posture. By dividing the network into smaller, isolated segments, microsegmentation limits the lateral movement of threats. If an attacker compromises one part of the network, they are unable to move freely across other segments, reducing the overall impact of the breach.
For example, if malware infiltrates one segment of the network, microsegmentation ensures it cannot spread to other parts of the system. This containment significantly lowers the risk of widespread damage, providing an additional layer of protection against cyber threats.
- Regulatory Compliance
Organizations in industries such as healthcare, finance, and retail must adhere to stringent data protection regulations, such as HIPAA, GDPR, and PCI-DSS. Microsegmentation helps businesses meet these compliance requirements by ensuring that sensitive data is isolated and access to it is tightly controlled.
By segmenting networks and creating strict security rules for each segment, microsegmentation makes it easier to track and control access, ensuring that only authorized individuals can access sensitive information. This level of control simplifies the auditing process and helps businesses avoid costly fines and penalties for non-compliance.
- Cost Efficiency
While the initial implementation of microsegmentation may incur some costs, it provides significant long-term savings. The ability to contain breaches within isolated segments prevents large-scale data leaks, reducing the financial impact of a security breach.
Furthermore, microsegmentation helps businesses save on operational costs by reducing the complexity of network security management. By providing a clear view of network traffic and enabling granular policy enforcement, organizations can respond more efficiently to threats, cutting down on downtime and minimizing disruptions to business operations.
- Flexibility Across Different IT Environments
Microsegmentation is highly adaptable, making it ideal for organizations with diverse IT environments, including cloud, hybrid, and on-premises infrastructures. Traditional network security solutions often struggle to provide robust security across these varied environments, but microsegmentation solutions like Illumio, Akamai, and VMware excel in these settings.
For instance, Akamai microsegmentation provides seamless integration with cloud environments, ensuring that even in dynamic, multi-cloud architectures, network segments remain secure. This adaptability makes microsegmentation a smart choice for businesses that are increasingly adopting cloud-based or hybrid infrastructure.
- Improved Visibility and Control
Microsegmentation offers enhanced visibility into network traffic, allowing businesses to monitor and analyze how data moves across the network. This level of visibility is crucial for identifying unusual behavior or potential threats early on. With real-time monitoring and granular access control, organizations can quickly detect and respond to security issues before they escalate.
Moreover, this visibility helps organizations understand their network’s vulnerabilities, enabling them to adjust security measures as needed and further bolster their defenses.
SEE ALSO: Best Branch Network Service for Enhanced Security in 2025
Top Microsegmentation Vendors and Solutions
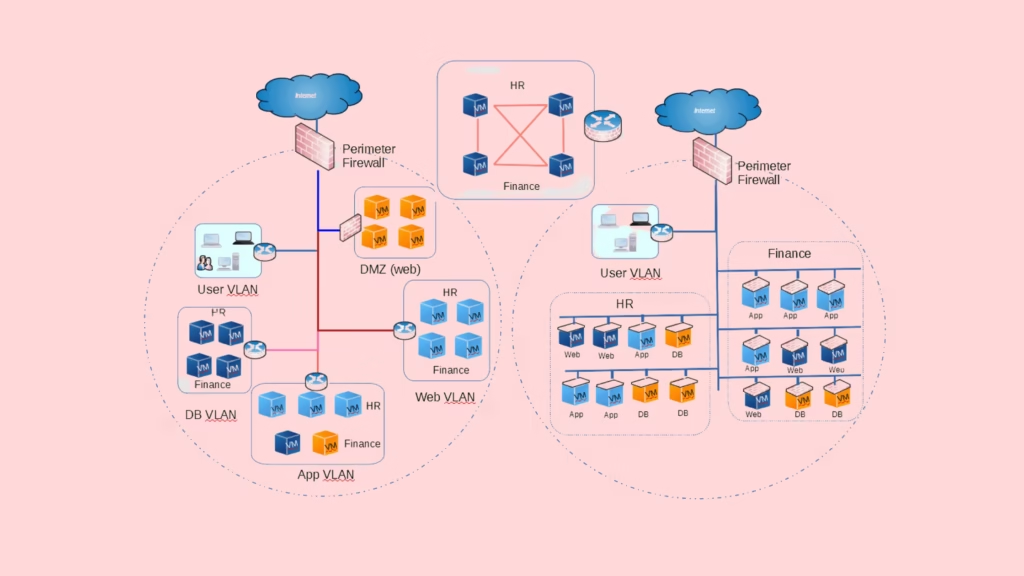
When it comes to implementing microsegmentation in a Zero Trust framework, several vendors lead the charge with advanced solutions designed to enhance network security. Below, we explore some of the top microsegmentation vendors that offer the best solutions for modern cybersecurity.
- Illumio
Illumio is one of the most prominent names in the microsegmentation space. Their platform is designed to provide granular Zero Trust segmentation for both on-premise and cloud environments. Illumio’s approach is particularly powerful in hybrid IT settings, offering visibility into how applications, workloads, and data interact across the network.
- Key Features:
- Zero Trust Segmentation: Illumio ensures that sensitive applications and workloads are isolated from each other, preventing lateral movement of threats across the network.
- Adaptive Security Policies: The solution allows businesses to create dynamic security policies that automatically adapt to changes in the network, without disrupting operations.
- Visibility and Risk Mapping: Illumio’s platform offers clear visibility into network traffic, identifying potential risks and vulnerabilities, and allowing organizations to respond proactively.
- Zero Trust Segmentation: Illumio ensures that sensitive applications and workloads are isolated from each other, preventing lateral movement of threats across the network.
Illumio’s solution is highly regarded for its ease of deployment and ability to scale, making it an excellent choice for businesses that require a flexible, highly secure system.
- Akamai Guardicore
Akamai Guardicore is another leader in the microsegmentation space, known for its user-friendly approach to Zero Trust. Guardicore enables businesses to enforce Zero Trust microsegmentation policies across both traditional and cloud-based infrastructures.
- Key Features:
- Rapid Deployment: Unlike many other microsegmentation solutions, Akamai Guardicore is designed for fast deployment without the need for complex network re-architecture.
- Visual Security Mapping: The platform offers detailed visual representations of network traffic, helping teams easily identify and manage security risks.
- Policy Enforcement: Guardicore provides robust security controls, ensuring that only authorized communications can take place between different segments of the network.
- Rapid Deployment: Unlike many other microsegmentation solutions, Akamai Guardicore is designed for fast deployment without the need for complex network re-architecture.
Akamai Guardicore stands out for its ease of use and quick deployment, making it a popular choice for organizations that want to quickly integrate microsegmentation into their cybersecurity strategy.
- VMware NSX
VMware NSX is a powerful microsegmentation solution that integrates seamlessly with VMware’s virtualization platform. It is particularly effective in virtualized and cloud environments, where traditional network security approaches are less effective.
- Key Features:
- Network Virtualization: VMware NSX allows businesses to create virtual networks and apply microsegmentation policies at the virtual network layer, offering fine-grained control over network traffic.
- Security at Scale: VMware’s platform enables security measures to be applied consistently across large, complex networks, making it suitable for enterprises with substantial IT environments.
- Compliance and Auditing: NSX helps organizations meet regulatory requirements by providing robust tools for auditing, monitoring, and reporting on network traffic.
- Network Virtualization: VMware NSX allows businesses to create virtual networks and apply microsegmentation policies at the virtual network layer, offering fine-grained control over network traffic.
VMware NSX is an excellent solution for organizations that have already invested heavily in VMware’s ecosystem and need a seamless way to implement Zero Trust microsegmentation within their virtualized environments.
- Cisco Secure Workload
Cisco Secure Workload is a comprehensive solution for securing application workloads across on-premises data centers, multi-cloud environments, and hybrid IT infrastructures. Cisco’s microsegmentation solution is built to integrate with existing security tools, providing enhanced visibility and control.
- Key Features:
- Cloud and Data Center Protection: Cisco’s solution is designed to secure workloads and applications, regardless of whether they are hosted on-premises or in the cloud.
- Continuous Monitoring: The platform provides continuous monitoring of applications and workloads to ensure that any unauthorized access or behavior is flagged immediately.
- Granular Security Policies: Cisco allows businesses to define detailed security policies that can be enforced across the entire network, limiting access and mitigating risk.
- Cloud and Data Center Protection: Cisco’s solution is designed to secure workloads and applications, regardless of whether they are hosted on-premises or in the cloud.
Cisco Secure Workload is particularly suited for organizations that need to secure a diverse IT infrastructure, including both cloud and on-prem environments.
READ ON: 20 Top Influencers in Cybersecurity for Job Seekers & Pros (USA, UK, and Canada)
Gartner Magic Quadrant for Microsegmentation Solutions
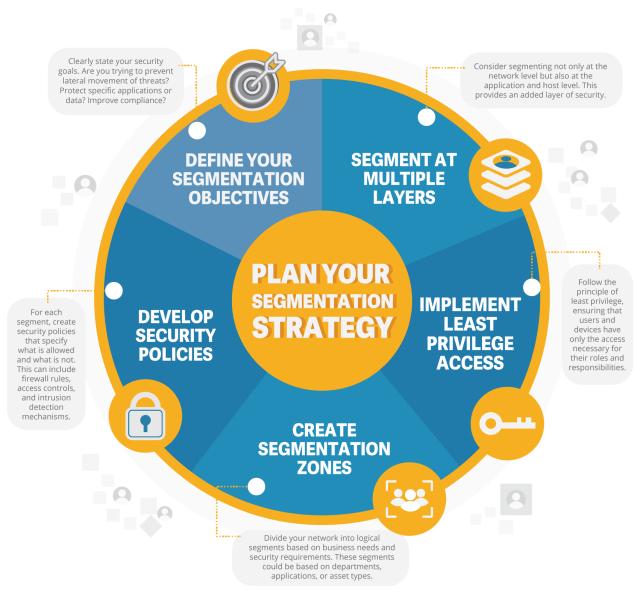
The Gartner Magic Quadrant is a research methodology that provides a graphical representation of a market’s direction, maturity, and participants. Gartner evaluates vendors based on their ability to execute and their completeness of vision, placing them into one of four categories:
- Leaders: Companies that are performing well in both execution and vision.
- Challengers: Companies that excel in execution but may lack a comprehensive vision.
- Visionaries: Companies that demonstrate an innovative approach but may struggle with execution.
- Niche Players: Companies that focus on a specific segment or market and may not have the broad capabilities of larger players.
For businesses looking to implement Zero Trust microsegmentation, the Gartner Magic Quadrant provides valuable insights into the top vendors, their strengths, and weaknesses, helping organizations make more informed decisions when selecting a solution.
Top Players in the Gartner Magic Quadrant for Microsegmentation
Several vendors consistently rank highly in Gartner’s Magic Quadrant for microsegmentation solutions. These companies are recognized for their innovation, execution, and ability to adapt to the increasing needs of the cybersecurity field.
- Illumio
- Illumio has been recognized as a Leader in the Gartner Magic Quadrant, thanks to its advanced capabilities in Zero Trust segmentation. The platform’s flexibility and scalability make it a standout, particularly for hybrid and multi-cloud environments.
- Strengths: Strong visibility and control, integration with diverse infrastructures, ease of deployment.
- Gartner’s View: Illumio is praised for its comprehensive security approach and ability to deliver microsegmentation at scale.
- Illumio has been recognized as a Leader in the Gartner Magic Quadrant, thanks to its advanced capabilities in Zero Trust segmentation. The platform’s flexibility and scalability make it a standout, particularly for hybrid and multi-cloud environments.
- Akamai Guardicore
- Akamai Guardicore is frequently featured as a Leader or Challenger in the Gartner Magic Quadrant. Known for its ease of use and rapid deployment, Guardicore is a solid choice for businesses looking for a simple and effective microsegmentation solution.
- Strengths: Speed of deployment, intuitive interface, strong visual mapping of network traffic.
- Gartner’s View: Akamai Guardicore’s solution excels in simplifying the deployment of Zero Trust microsegmentation, but may face limitations in very large-scale environments.
- Akamai Guardicore is frequently featured as a Leader or Challenger in the Gartner Magic Quadrant. Known for its ease of use and rapid deployment, Guardicore is a solid choice for businesses looking for a simple and effective microsegmentation solution.
- VMware NSX
- VMware NSX consistently ranks as a Leader in the Gartner Magic Quadrant for microsegmentation solutions, particularly in virtualized environments. VMware’s strong presence in virtualization allows it to provide robust network security through microsegmentation.
- Strengths: Integration with VMware ecosystem, scalability, detailed security policies.
- Gartner’s View: VMware is noted for its strong execution, particularly in virtualized and cloud environments, but its solution may not be as flexible outside of the VMware ecosystem.
- VMware NSX consistently ranks as a Leader in the Gartner Magic Quadrant for microsegmentation solutions, particularly in virtualized environments. VMware’s strong presence in virtualization allows it to provide robust network security through microsegmentation.
- Cisco Secure Workload
- Cisco Secure Workload is often ranked as a Leader or Challenger, offering comprehensive security for both on-premises and cloud-based workloads. Cisco’s solution is particularly strong in large enterprises with complex IT infrastructures.
- Strengths: Continuous monitoring, granular security policies, extensive integration capabilities.
- Gartner’s View: Cisco’s solution is praised for its strong focus on securing workloads and applications, particularly in hybrid environments, but may require more configuration and expertise than some other solutions.
- Cisco Secure Workload is often ranked as a Leader or Challenger, offering comprehensive security for both on-premises and cloud-based workloads. Cisco’s solution is particularly strong in large enterprises with complex IT infrastructures.
Gartner’s Magic Quadrant provides businesses with an unbiased, expert assessment of the top players in the microsegmentation market. The rankings are based on both the vendor’s ability to execute and its completeness of vision, offering an easy-to-understand visual representation of where each vendor stands in the market.
By referring to the Magic Quadrant, businesses can make data-driven decisions about which vendor will best meet their cybersecurity needs.
For instance, if an organization prioritizes ease of deployment and quick integration, they might prefer Akamai Guardicore. On the other hand, businesses requiring scalability and deep integration with cloud and on-prem environments might lean towards Illumio or VMware NSX.
ALSO: What Is Tradecraft in Cybersecurity? What Businesses Need to Know in 2025
Comparing the Best Solutions: Illumio, Akamai, and VMware

With numerous microsegmentation solutions on the market, it’s essential for businesses to choose the one that best aligns with their specific needs. In this section, we’ll compare three of the top Zero Trust microsegmentation solutions: Illumio, Akamai Guardicore, and VMware NSX. Each of these solutions has its unique strengths and may suit different organizational requirements.
Illumio vs. Akamai Guardicore vs. VMware NSX: A Comparison
| Feature | Illumio | Akamai Guardicore | VMware NSX |
| Deployment Speed | Fast deployment with minimal disruption | Rapid deployment with minimal network changes | Slower deployment due to integration with VMware ecosystem |
| Scalability | Highly scalable, ideal for hybrid and multi-cloud environments | Scalable, but may be more suited for smaller-to-medium enterprises | Excellent scalability, especially for large-scale virtualized environments |
| Ease of Use | User-friendly with robust visibility and control | Intuitive interface, easy to navigate | Requires VMware expertise, more complex than others |
| Integration | Works well with various cloud and on-prem systems | Seamlessly integrates with cloud environments | Best suited for organizations already using VMware products |
| Zero Trust Features | Strong Zero Trust capabilities with deep network segmentation | Effective Zero Trust with visual mapping of network traffic | Advanced security but requires deep VMware integration for full Zero Trust capabilities |
| Regulatory Compliance | Helps meet compliance standards like HIPAA, PCI-DSS, GDPR | Provides compliance capabilities, especially in cloud environments | Excellent for compliance, particularly in virtualized environments |
| Support and Training | Offers extensive support with flexible resources | Provides strong customer support, but requires training for complex use | Offers strong support but may require VMware-specific training |
How to Implement Zero Trust Microsegmentation in Your Organization

Implementing Zero Trust microsegmentation within an organization can greatly enhance network security by reducing attack surfaces and preventing lateral movement of threats. However, the process requires careful planning and execution to ensure that the solution integrates smoothly into existing IT infrastructures. Below, we outline the key steps involved in implementing microsegmentation and the Zero Trust approach.
1. Map Network Traffic
The first step in implementing microsegmentation is understanding how different parts of the network communicate with each other. This step is critical as it helps identify critical assets, potential vulnerabilities, and network dependencies. Tools like Illumio and Akamai Guardicore provide visibility into network traffic, making it easier to understand how applications, devices, and workloads interact.
- What to do:
- Use network mapping tools to visualize traffic flow.
- Identify sensitive workloads, data, and applications that require tighter controls.
- Determine communication patterns between systems and devices.
- Use network mapping tools to visualize traffic flow.
2. Define Policies
Once you’ve mapped network traffic, the next step is to create security policies that enforce least privilege access, only allowing necessary communications between network segments. These policies should be based on the principle of Zero Trust, ensuring that all access is verified and authenticated before being granted.
- What to do:
- Identify the resources that need protection and define access policies based on user roles and needs.
- Ensure policies enforce only necessary connections, isolating critical systems and sensitive data.
- Customize policies to suit specific network environments (cloud, hybrid, on-prem).
- Identify the resources that need protection and define access policies based on user roles and needs.
3. Apply Controls
With policies in place, the next step is to implement controls that enforce those policies. Microsegmentation solutions like VMware NSX, Illumio, and Akamai Guardicore provide the tools to enforce segmentation and control network traffic flow according to defined policies.
- What to do:
- Apply microsegmentation tools to enforce policies across your network.
- Use virtual firewalls and access controls to segment the network.
- Ensure that traffic between segments is restricted based on defined security policies.
- Apply microsegmentation tools to enforce policies across your network.
4. Monitor and Adjust
Microsegmentation is not a set-it-and-forget-it solution; it requires ongoing monitoring to ensure that it is functioning as intended and to respond to new threats. Continuous monitoring helps detect any anomalies or unauthorized access attempts, allowing you to adjust security policies as needed.
- What to do:
- Set up monitoring tools to track network traffic and detect abnormal behavior.
- Adjust policies and access controls as necessary based on real-time data and emerging threats.
- Use tools like Illumio and Akamai Guardicore to continuously analyze and adjust security measures.
- Set up monitoring tools to track network traffic and detect abnormal behavior.
5. Educate and Train Teams
Implementing microsegmentation requires collaboration from multiple departments, especially IT and security teams. Proper training is essential to ensure that team members understand how the microsegmentation solution works, how to apply policies, and how to react to potential security incidents.
- What to do:
- Provide training for IT and security teams on microsegmentation concepts and best practices.
- Educate staff on the importance of the Zero Trust model and how it fits into the organization’s overall security posture.
- Conduct regular drills and simulations to ensure the team is prepared to respond to security incidents effectively.
- Provide training for IT and security teams on microsegmentation concepts and best practices.
Key Considerations for a Successful Implementation
While the technical aspects of microsegmentation are important, successful implementation also requires attention to the organizational and procedural elements:
- Scalability: Ensure that the chosen microsegmentation solution can scale as your organization grows. Solutions like Illumio are designed to grow with your organization’s needs.
- Compatibility: Consider how well the solution integrates with existing infrastructure and security tools.
- Performance Impact: Microsegmentation can introduce performance overhead. Choose a solution that balances security with minimal disruption to network performance.
Challenges to Anticipate
- Legacy Systems: Many organizations struggle to integrate microsegmentation with legacy IT systems that may not support modern security protocols.
- Complexity in Large Networks: In large, complex networks, defining policies and applying controls can be challenging, requiring careful planning and execution.
- Resistance to Change: Employees and IT staff accustomed to traditional network security approaches may be resistant to adopting a new system.
Conclusion
As cybersecurity threats continue to increase, the need for robust, adaptive solutions has never been more pressing. Zero Trust and microsegmentation offer critical strategies to safeguard sensitive data, minimize attack surfaces, and ensure that threats are contained within isolated segments of a network.
By implementing these principles, organizations can create a security framework where access is rigorously controlled, and every transaction or access request is verified, no exceptions.
Illumio, Akamai Guardicore, and VMware NSX stand out as leaders in the microsegmentation space, each offering unique advantages tailored to different organizational needs. Whether you’re seeking scalability, ease of deployment, or seamless integration with existing infrastructure, these solutions provide the flexibility and control necessary to build a resilient cybersecurity posture.
Choosing the right Zero Trust microsegmentation solution is not a one-size-fits-all decision—it depends on factors like infrastructure complexity, regulatory requirements, and the desired level of granularity. However, the benefits are undeniable: improved security, compliance, reduced costs from breaches, and better visibility into network traffic.
By adopting microsegmentation as part of a Zero Trust strategy, businesses can better protect themselves against modern threats, limit potential damage from attacks, and stay ahead of increasingly sophisticated cyber adversaries. As the cybersecurity landscape continues to evolve, these solutions are not just an option; they’re a necessity.
Now is the time to strengthen your organization’s defenses with the best Zero Trust microsegmentation solutions and prepare for the future of cybersecurity.
FAQ
How does Illumio’s microsegmentation solution work?
Illumio provides a Zero Trust microsegmentation platform that maps network traffic, segments applications and workloads, and enforces security policies to minimize lateral movement.
Its solution offers granular visibility into network traffic, enabling businesses to see potential risks and apply security controls based on the least privilege model. Illumio is highly scalable and works well in hybrid and multi-cloud environments.
What is the difference between microsegmentation and traditional network security?
Traditional network security typically uses broad zones, like a firewall separating an internal network from the internet. Microsegmentation, on the other hand, creates much smaller, isolated segments within the network, offering granular control over communication.
While traditional security often relies on perimeter defenses, microsegmentation provides deeper protection by controlling internal traffic and enforcing strict security policies across all network segments.
Can microsegmentation be implemented in hybrid or cloud environments?
Yes, microsegmentation can be implemented in hybrid and cloud environments. Solutions like Illumio and Akamai Guardicore are specifically designed to provide security in cloud and hybrid infrastructures.
These solutions ensure that sensitive data and applications are segmented and protected, regardless of whether they reside on-premises or in the cloud.

