What Is the First Step in Cyber Security Strategy?
Businesses face an ever-growing array of cyber threats that can disrupt operations, compromise data, and damage reputations. With the rise of advanced attacks like ransomware and data breaches, a strong cybersecurity strategy has become a necessity.
But how do you build such a strategy? The first step is crucial to ensuring your organization’s cybersecurity posture remains resilient.
The first step in developing a cybersecurity strategy isn’t just about implementing the latest tools or technologies; it’s about understanding the unique threats that your organization faces. This foundational stage sets the direction for all subsequent actions and helps prioritize the efforts that will safeguard your assets, reputation, and overall business success.
This article will answer the question: what is the first step in cyber security strategy? We will explain why it’s so important and how organizations can approach it with a solid framework for long-term success.

RELATED: Domain Cyber Threats: Everything You Need to Know
The Importance of Cybersecurity Strategy
Before diving into the specifics of the first step, it’s essential to understand why a cybersecurity strategy is so important. A cybersecurity strategy provides a structured, high-level plan to protect your organization’s assets, data, and systems from evolving cyber threats.
It ensures that all security measures are aligned with business goals, and it outlines how to prevent, detect, and respond to cyber incidents.
A cybersecurity strategy also helps establish a clear path for cybersecurity implementation and resource allocation. It turns abstract security concerns into concrete actions that can be measured and improved over time. Without a strategy in place, organizations risk reacting to cyber threats as they arise rather than taking a proactive approach to prevent them.
Consider a cyber security strategy example: A large financial institution recently faced an escalating number of ransomware attacks. By implementing a well-defined strategy, assessing risks, identifying critical assets, and aligning their security measures with business goals, they were able to fortify their defenses.
This proactive approach significantly reduced their vulnerability and limited the damage caused by future attacks.
The ultimate goal of a cybersecurity strategy is to minimize risks while maximizing the security of critical assets, networks, and systems. This first step is foundational in guiding the rest of the organization’s efforts, ensuring all subsequent actions are well-prioritized and aligned with overarching security objectives.
Step 1: Assessing the Cyber Threat Landscape

The very first step in any cybersecurity strategy is to assess the cyber threats. This initial step involves understanding what types of threats your organization is most likely to encounter and what risks these threats pose to your systems, data, and overall operations.
It is a critical starting point, as it allows you to tailor your security strategy to address the most pressing and relevant risks rather than applying generic solutions that may not be as effective.
What Does Cyber Threat Include?
A cyber threat landscape is essentially a map of potential threats and vulnerabilities that could impact your business. It includes both current and emerging cyber risks, such as:
- Ransomware: These attacks often lock down critical data and demand a ransom for its release, posing significant financial and reputational damage to organizations.
- Phishing and Social Engineering: Cybercriminals may exploit human vulnerabilities through email or other communication channels to steal sensitive information.
- Malware: Malicious software that infiltrates and damages systems, often without the user’s knowledge.
- Insider Threats: These involve employees or contractors using their access to data or systems maliciously or negligently.
- Supply Chain Attacks: Exploiting vulnerabilities in third-party vendors or partners to infiltrate an organization’s systems.
Additionally, it is essential to stay ahead of emerging threats, such as the increasing risk of cyber-attacks targeting cloud infrastructure and Internet of Things (IoT) devices.
By identifying the types of attacks that are most prevalent in your industry or sector, you can better prepare and prioritize resources to counter those risks.
For example, financial institutions may face a greater threat from advanced persistent threats (APTs) or supply chain vulnerabilities, while small businesses might be more susceptible to phishing or ransomware attacks.
READ MORE: Map of Cybersecurity Domain: A Complete Analysis
Cybersecurity Strategy and Implementation Plan
Once you have a clear understanding of the cyber threat landscape, you can begin crafting your cybersecurity strategy and implementation plan. This will focus on addressing the specific risks identified during your assessment.
For example, if ransomware is deemed a high risk, your strategy may include advanced backup and recovery systems, along with employee training to recognize phishing attempts.
The NIST Cybersecurity Strategy Template offers a structured approach to assessing threats. This framework helps organizations categorize risks based on likelihood and impact, ensuring that the most severe threats receive the most attention.
This template also guides the development of a security strategy by laying out specific cybersecurity controls and activities that need to be implemented depending on the identified risks.
With a clear understanding of your cyber threat landscape, your cybersecurity strategy becomes more focused, effective, and aligned with actual risks, allowing your organization to better protect its assets and data from cyber threats.
Utilizing Cybersecurity Frameworks to Build Strategy

Once the cyber threat landscape has been assessed, the next step is to utilize established cybersecurity frameworks to structure your strategy.
Frameworks like the NIST Cybersecurity Framework and CISA’s Cybersecurity Plan Template provide organizations with structured guidance for developing comprehensive cybersecurity strategies. They offer templates and guidelines that help ensure a systematic and holistic approach to cybersecurity.
NIST Cybersecurity Strategy Template
The NIST Cybersecurity Strategy Template is one of the most widely adopted frameworks in cybersecurity. Developed by the National Institute of Standards and Technology, the NIST framework provides a comprehensive structure for developing a cybersecurity strategy. It includes detailed steps for:
- Identifying critical assets: Knowing what needs protection, such as customer data, financial records, intellectual property, etc.
- Protecting those assets: This includes implementing the right technologies and processes, such as encryption, multi-factor authentication, and network segmentation.
- Detecting potential threats: Real-time monitoring of systems to spot anomalies and breaches as soon as they happen.
- Responding to incidents: Having a clear, actionable plan to contain and mitigate damage during and after an attack.
- Recovering from cyber incidents: Ensuring business continuity with disaster recovery plans and backup systems.
By utilizing the NIST Cybersecurity Strategy Template, organizations can ensure that they are building a strategy that not only meets their specific needs but also aligns with industry best practices. The template offers flexibility to adapt the strategy based on the organization’s size, industry, and risk profile, making it an ideal choice for businesses of all types.
ALSO SEE: What Is the First Step in Creating Cybersecurity Controls?
Cybersecurity Plan Template CISA
Similarly, the Cybersecurity Plan Template CISA (Cybersecurity and Infrastructure Security Agency) provides another valuable resource for organizations developing their cybersecurity strategy. This template offers a more hands-on approach, giving practical steps to implement security controls, perform risk assessments, and evaluate vulnerabilities within the organization.
The CISA template is especially helpful for smaller organizations or those without dedicated cybersecurity teams, as it simplifies complex processes and lays out clear actions for improving security.
CISA’s template also encourages collaboration across different departments, ensuring that cybersecurity is not just the responsibility of the IT team but is embedded within the organization’s broader operational processes.
This collaborative approach ensures a culture of security where everyone in the organization, from leadership to entry-level employees, understands their role in maintaining cybersecurity.
Using frameworks like NIST and CISA not only provides a proven path for developing a cybersecurity strategy but also ensures that the organization remains compliant with regulatory standards and best practices in the industry.
Understanding Organizational Risks and Assets
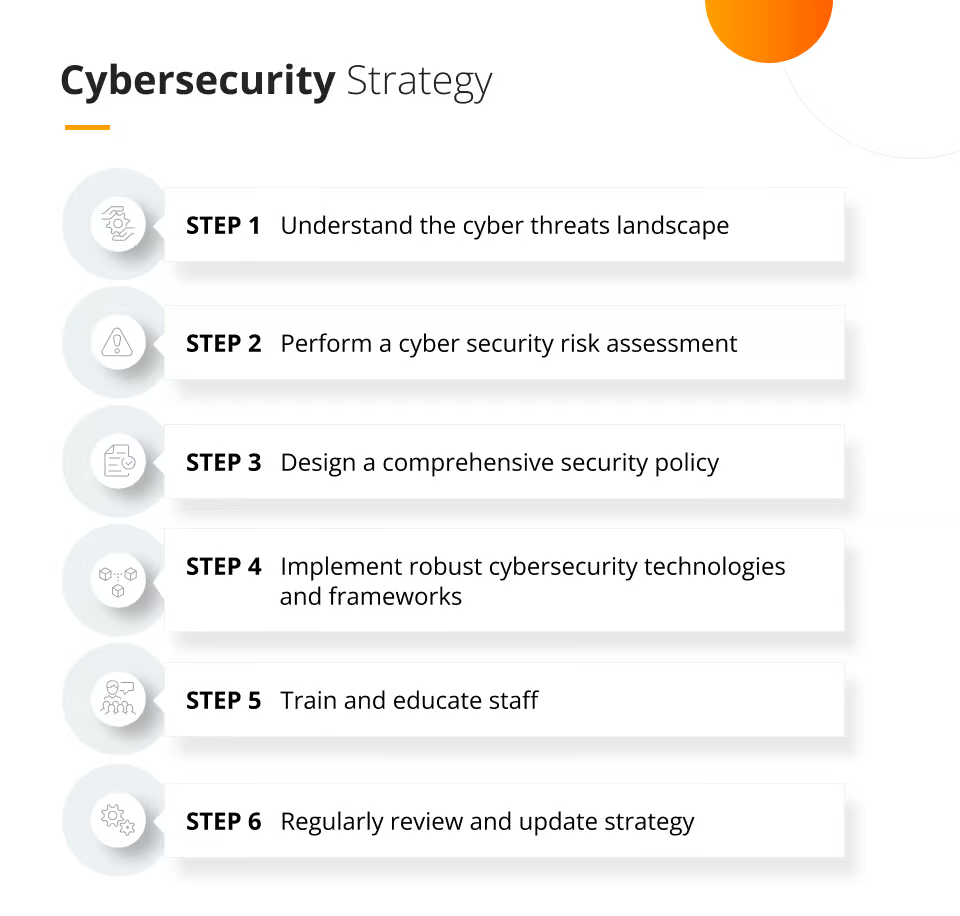
Now that we have a structured understanding of the cyber threat landscape and frameworks, it’s essential to focus on the next critical step: identifying organizational risks and assets. This step is about understanding what needs protection, why it’s crucial, and how to prioritize resources to defend these assets from the most significant risks.
Identifying Critical Assets
The first part of understanding organizational risks is identifying your critical assets. These are the resources, systems, and data that are vital to the operation of your business. Identifying them helps you focus your cybersecurity strategy on protecting what matters most. Examples of critical assets include:
- Customer Data: This may include personally identifiable information (PII), financial records, and transaction data. A breach of customer data can lead to significant financial and reputational damage.
- Intellectual Property (IP): Companies rely on proprietary technologies, business models, and innovations that, if stolen, could result in losing competitive advantages.
- Financial Systems and Data: These are crucial for daily operations, and if compromised, they can lead to severe financial loss and disruption.
- Human Resources Data: Employee data, such as payroll and benefits information, is another critical asset that needs to be protected.
Identifying these assets is the first step in ensuring they’re given the proper level of protection. Different types of assets will require different levels of security measures depending on their criticality to the organization’s operations.
Evaluating Risks
Once the critical assets are identified, the next task is to evaluate the risks they face. Every asset carries a potential risk that could harm the organization, whether it’s the loss of data, financial damage, or damage to brand reputation. Evaluating risks involves answering a few key questions:
- What threats could exploit vulnerabilities in our assets?
- How likely are these threats to occur?
- What would be the impact if these threats came to fruition?
This risk evaluation process is vital in helping prioritize efforts. For instance, if ransomware is identified as a top threat, the organization can prioritize enhancing backup and recovery protocols or improving employee awareness to prevent phishing.
A good approach is to use a risk matrix, which helps to categorize threats by their likelihood and potential impact. This approach ensures that the most critical threats are addressed first, optimizing resource allocation.
Cybersecurity Strategy Implementation Plan
Once the risks are evaluated, this information is integrated into the cybersecurity strategy and implementation plan. The strategy needs to reflect the specific threats and risks identified, helping the organization allocate the right resources to safeguard the most valuable assets.
For example, if intellectual property is a high-risk asset, investing in robust access control and encryption measures may be necessary.
Moreover, the cybersecurity implementation project plan should outline specific tasks, timelines, and responsibilities, ensuring that all elements of the strategy are executed efficiently and effectively.
By identifying assets and evaluating risks, organizations can ensure that their cybersecurity strategy is tailored to their unique needs, increasing their ability to protect critical assets and reduce overall exposure to cyber threats.
MORE: What Is ALE in Cyber Security? Calculating Cyber Risk, SLE, SLA, RTO
Analyzing Cybersecurity Maturity and Preparing for Improvement

With a clear understanding of the cyber threat landscape and identified critical assets and risks, the next step in building a comprehensive cybersecurity strategy is to assess your organization’s current cybersecurity maturity.
This step is vital for understanding where your organization currently stands in terms of security capabilities, identifying gaps, and setting objectives for improvement over the next few years.
Assessing Cybersecurity Maturity
Cybersecurity maturity refers to an organization’s ability to effectively manage and mitigate risks through a combination of processes, policies, technologies, and trained personnel. It encompasses various aspects of cybersecurity, including governance, incident management, risk management, and technical defenses.
Understanding your organization’s maturity allows you to create a roadmap for improvement that aligns with your strategic goals.
To assess cybersecurity maturity, organizations often use frameworks like the NIST Cybersecurity Framework or the CISA Cybersecurity Plan Template, both of which offer guidance on assessing current capabilities and setting future goals.
A cybersecurity maturity assessment typically involves evaluating your organization’s existing controls and processes in areas such as:
- Governance and policies: Does your organization have well-defined cybersecurity policies, and are they enforced across departments?
- Incident response: How effective is your incident response plan? Does your organization have a clear, practiced approach for handling breaches?
- Risk management: Is there a formal risk management process in place, and is it regularly updated to reflect evolving threats?
- Technology and tools: Does your organization use the appropriate tools and technologies to safeguard assets, and are they up to date?
This assessment not only helps pinpoint weaknesses but also provides a baseline for measuring improvement.
Cyber Security Implementation Project Plan
Following the maturity assessment, the next step is to integrate the results into a cybersecurity implementation project plan. This plan outlines the specific actions required to move your organization from its current maturity level to a desired future state. It includes:
- Setting clear objectives: Define what success looks like at each stage of the implementation.
- Allocating resources: Determine the budget, staff, and tools required to improve security capabilities.
- Prioritizing actions: Based on the risk evaluation and maturity assessment, prioritize actions that will have the most significant impact on reducing vulnerabilities.
- Timeline and milestones: Set timelines for implementing new processes or technologies and identify key milestones to track progress.
By using a structured cybersecurity implementation project plan, organizations can ensure that their efforts are focused on achieving measurable improvements over time and addressing the most pressing security gaps.
Cybersecurity Strategy and Implementation Plan
This leads to the creation of a more refined cybersecurity strategy and implementation plan. With a solid understanding of the current state, a clear assessment of gaps, and a roadmap for improvement, the organization is now in a better position to set realistic goals, track progress, and adjust strategies as necessary.
By assessing cybersecurity maturity early on, businesses can avoid the pitfall of implementing costly or unnecessary measures without understanding their current needs. Instead, they can take a more strategic, incremental approach to building a robust, future-proof cybersecurity posture.
READ: What Is the Slam Method in Cyber Security?
Best Practices for Conducting a Cyber Threat Assessment

Now that we’ve established the importance of understanding your cyber threat landscape, it’s essential to deeply understand the best practices for conducting a thorough assessment.
A well-executed cyber threat landscape evaluation forms the backbone of your cybersecurity strategy and can help identify vulnerabilities, potential threats, and areas for improvement. The following practices are key to ensuring that your assessment is effective and comprehensive.
1. Collecting Threat Intelligence
Threat intelligence is critical for understanding the current and future landscape of cyber risks. It involves gathering data from various sources to anticipate and defend against potential cyber threats. Threat intelligence can come from:
- Industry reports: Many organizations and government agencies release regular cybersecurity threat reports. Sources like the National Cybersecurity Strategy or CISA often provide updates on emerging threats and attack trends.
- External threat feeds: Subscribing to threat intelligence feeds can provide real-time alerts about vulnerabilities or attacks targeting specific industries or technologies.
- Threat-sharing networks: Joining cybersecurity communities or industry-specific networks can provide insights into threats faced by similar organizations and offer collaboration opportunities for mitigation.
2. Engaging with Industry Experts
While collecting threat intelligence is essential, it’s equally important to seek guidance from cybersecurity experts. This could include engaging with external consultants, cybersecurity firms, or even industry peers. These experts can help interpret complex data, provide deeper insights into specific threats, and recommend tailored cybersecurity measures.
For example, if your organization is in the healthcare industry, working with experts in HIPAA compliance and healthcare-specific cybersecurity risks can ensure that your assessment is focused on the most relevant threats, such as data breaches and insider threats.
3. Simulating Cyber Attacks
One of the most effective ways to understand the vulnerabilities in your system is through penetration testing or red team exercises. These simulations involve cybersecurity professionals attempting to breach your systems using the same tactics as real-world attackers.
Penetration testing allows you to see how well your defenses hold up against specific types of attacks, such as social engineering, ransomware, or phishing. Red team exercises, which simulate full-scale cyberattacks, help identify weaknesses in not only your technology but also your organization’s response to incidents.
4. Collaborating with Third-Party Security Vendors
Working with third-party security vendors is also a key best practice. These vendors bring specialized tools, technologies, and expertise to the table. Some vendors provide advanced intrusion detection systems (IDS), endpoint protection, or cloud security services that can be used to assess your existing security posture.
By collaborating with these vendors, organizations can augment their internal resources and gain access to cutting-edge technologies that help identify gaps in their cybersecurity strategy. Moreover, third-party security assessments can offer a fresh perspective on security vulnerabilities that internal teams might overlook.
5. Continuous Monitoring and Feedback Loops
A static assessment is not enough. Continuous monitoring is crucial for identifying and mitigating threats in real-time. Implementing tools such as Security Information and Event Management (SIEM) systems can provide 24/7 monitoring of your networks and systems.
These tools can help you identify suspicious activity, anomalous behavior, or potential breaches quickly.
Additionally, feedback loops from monitoring tools and regular vulnerability assessments can help adjust and improve your cybersecurity strategy over time. This ensures that your strategy remains relevant in an ever-evolving threat landscape.
6. Reporting and Documentation
Documenting your threat landscape assessment findings is essential for establishing a clear record of identified threats, vulnerabilities, and potential impacts on the organization. This documentation should be thorough, including data on how each risk was identified, its potential consequences, and the proposed mitigation strategies.
Having a cybersecurity plan template CISA or similar framework can help structure your documentation and ensure that it aligns with industry standards. This documentation is not only useful for internal reference but is also essential for compliance with industry regulations and external audits.
7. Engaging Employees in the Process
Cyber threats often target the human element, so it’s vital to engage employees in the threat landscape assessment process. Employees are on the front lines and can provide valuable insights into potential vulnerabilities. For example, understanding how employees interact with email or social media can highlight areas where phishing attacks might be most successful.
Engaging employees through awareness programs or cybersecurity training is essential. Training helps create a culture of security, ensuring that staff members are aware of potential threats and know how to react when they identify something suspicious.
Conclusion
The first step in building a robust cybersecurity strategy is undoubtedly the assessment of your cyber threats. This foundational process helps organizations understand the specific risks they face, prioritize assets that require protection, and align their efforts with realistic, data-driven objectives.
By identifying threats and vulnerabilities, businesses can allocate resources more effectively, ensuring that their cybersecurity measures are focused on what matters most.
By utilizing established frameworks like the NIST Cybersecurity Strategy Template and CISA’s Cybersecurity Plan Template, organizations can structure their threat assessments and ensure that their strategies align with industry best practices.
These templates not only provide valuable guidance but also help businesses create a comprehensive cybersecurity strategy and implementation plan.
The next steps after understanding threats, evaluating cybersecurity maturity, prioritizing actions, and implementing improvements are essential for building a long-term, adaptable cybersecurity framework. Cyber threats are ever-evolving, and only through continuous monitoring, adaptation, and employee engagement can organizations stay ahead of the curve.
Now that you have a clearer understanding of the importance of assessing your cyber threat landscape, it’s time to take action. Conduct a thorough threat assessment, use the right frameworks, and start building a cybersecurity strategy that safeguards your most valuable assets.
FAQ
What is the first step in cybersecurity?
The first step in cybersecurity is to assess the cyber threat landscape. This involves understanding the types of threats and vulnerabilities that could potentially impact your organization’s systems, data, and operations. By identifying existing and emerging cyber risks, businesses can prioritize which areas need the most attention and tailor their cybersecurity strategy to effectively mitigate these threats.
What is the first stage of cybersecurity?
The first stage of cybersecurity is to conduct a thorough risk assessment. This stage involves identifying critical assets, understanding potential threats, and evaluating vulnerabilities that could expose those assets to risks. A proper risk assessment helps establish a clear understanding of the security needs and forms the foundation for building a robust cybersecurity strategy.
What is the security-first strategy?
A security-first strategy is an approach where an organization prioritizes cybersecurity in every aspect of its operations and decision-making process. This strategy ensures that security is not an afterthought but is integrated into the design, development, and management of all systems, products, and services from the outset. By adopting a security-first mindset, organizations aim to protect their assets and reduce risks proactively rather than reacting to threats after they occur.
What is the strategy of cybersecurity?
The strategy of cybersecurity refers to the comprehensive, structured plan that an organization follows to protect its information systems, networks, and data from cyber threats. It includes the identification of assets, assessment of risks, and implementation of protective measures like firewalls, encryption, and access controls.
A good cybersecurity strategy also involves proactive steps like employee training, continuous monitoring, incident response plans, and regular updates to adapt to new threats. The ultimate goal is to minimize risks while ensuring that business operations can continue securely and efficiently.
If you’re ready to take the next step in your cybersecurity journey? You can do that with an expert beside you to guide you through without having to stress much. Schedule a one-on-one consultation with Tolulope Michael, a cybersecurity professional with over a decade of field experience. This will allow you to gain personalized insights and guidance tailored to your career goals.
Visit tolumichael.com now to book your session. This is your opportunity to embark on your cybersecurity career with confidence. Don’t miss out!

