What Is Best Plan for Data Loss Prevention (DLP)
Data is one of the most valuable assets of any organization. However, with increasing cyber threats, insider risks, and accidental data exposure, safeguarding sensitive information has become a top priority. A data loss prevention strategy is essential to protect sensitive data from being lost, leaked, or stolen.
Organizations need a structured approach to data loss prevention (DLP), one that integrates technology, policies, and employee awareness. Implementing a DLP project plan ensures that businesses can effectively prevent unauthorized access to confidential information while complying with industry regulations like GDPR, HIPAA, and PCI DSS.
This article explains what is best plan for data loss prevention and provides a DLP implementation checklist to guide organizations in building a comprehensive DLP strategy. From defining critical assets to implementing secure design strategies for data loss prevention, this guide will outline the best practices for protecting sensitive information.

RELATED: Is Cyber Security Analyst the Same as Incident Response Analyst?
What Is Data Loss Prevention (DLP)?
To implement the best plan for data loss prevention, it’s essential to first understand what DLP is and how it functions within an organization’s cybersecurity framework.
Data Loss Prevention (DLP) refers to a set of technologies, policies, and practices designed to prevent unauthorized access, loss, or leakage of sensitive information. It involves monitoring, detecting, and blocking sensitive data from being accessed or transmitted by unauthorized users.
DLP solutions focus on three key states of data:
- Data in Motion – Data traveling across a network (emails, file transfers, cloud sharing, etc.).
- Data at Rest – Data stored in databases, file systems, and cloud storage.
- Data in Use – Data being actively accessed or manipulated on endpoints like desktops, laptops, or mobile devices.
A well-designed DLP strategy ensures that sensitive business data, such as financial records, intellectual property, and customer information, remains secure across these three states.
Why is DLP Critical for Cybersecurity?
Organizations face multiple threats that can lead to data loss, including:
- Cyberattacks (e.g., ransomware, phishing, and data breaches).
- Insider threats (employees or contractors leaking sensitive data, either intentionally or accidentally).
- Compliance risks (failure to protect sensitive data can result in legal penalties).
- Human errors (misdirected emails, unsecured data sharing, or accidental file deletion).
A DLP implementation project plan helps organizations reduce these risks by proactively identifying and protecting sensitive data while ensuring compliance with data protection regulations.
READ MORE: Data Protection Vs Data Security: A Comprehensive Analysis
What Is the Best Plan for Data Loss Prevention in Cybersecurity?

A strong data loss prevention strategy must be comprehensive, proactive, and adaptable to evolving threats. The best plan for data loss prevention in cybersecurity involves a combination of policies, technology, and employee awareness to ensure that sensitive data is always protected.
Key Components of an Effective DLP Plan
To build a robust DLP implementation project plan, organizations should focus on the following core components:
- Data Classification & Risk Assessment
- Identify critical business data (e.g., financial records, intellectual property, customer data).
- Categorize data based on sensitivity levels (public, internal, confidential, restricted).
- Conduct a risk assessment to understand potential threats and vulnerabilities.
- Policy Development & Compliance Alignment
- Establish DLP policies that align with regulatory standards like GDPR, HIPAA, and PCI DSS.
- Define rules for data access, sharing, and storage across all business units.
- Ensure encryption, multi-factor authentication (MFA), and access controls are in place.
- Technology Implementation & Automation
- Deploy DLP software to monitor and control data movement across endpoints, networks, and cloud storage.
- Utilize SIEM (Security Information and Event Management) tools for real-time threat detection.
- Automate data classification, anomaly detection, and incident response workflows.
- Employee Awareness & Insider Threat Mitigation
- Conduct regular security awareness training to educate employees on phishing, insider threats, and safe data handling.
- Implement role-based access controls (RBAC) to limit data access based on job functions.
- Monitor user behavior analytics (UBA) to detect unusual activities that may indicate a data breach.
- Continuous Monitoring & Incident Response
- Establish a DLP incident response plan to contain and remediate breaches quickly.
- Conduct regular security audits to assess the effectiveness of DLP measures.
- Use AI-driven analytics to predict and prevent potential data loss scenarios.
By following these components, organizations can strengthen their cybersecurity posture and ensure their DLP project plan effectively prevents data leaks, insider threats, and cyberattacks.
SEE ALSO: Phishing Attack Examples, Types, and Prevention
Data Loss Prevention Methods: A Multi-Layered Approach
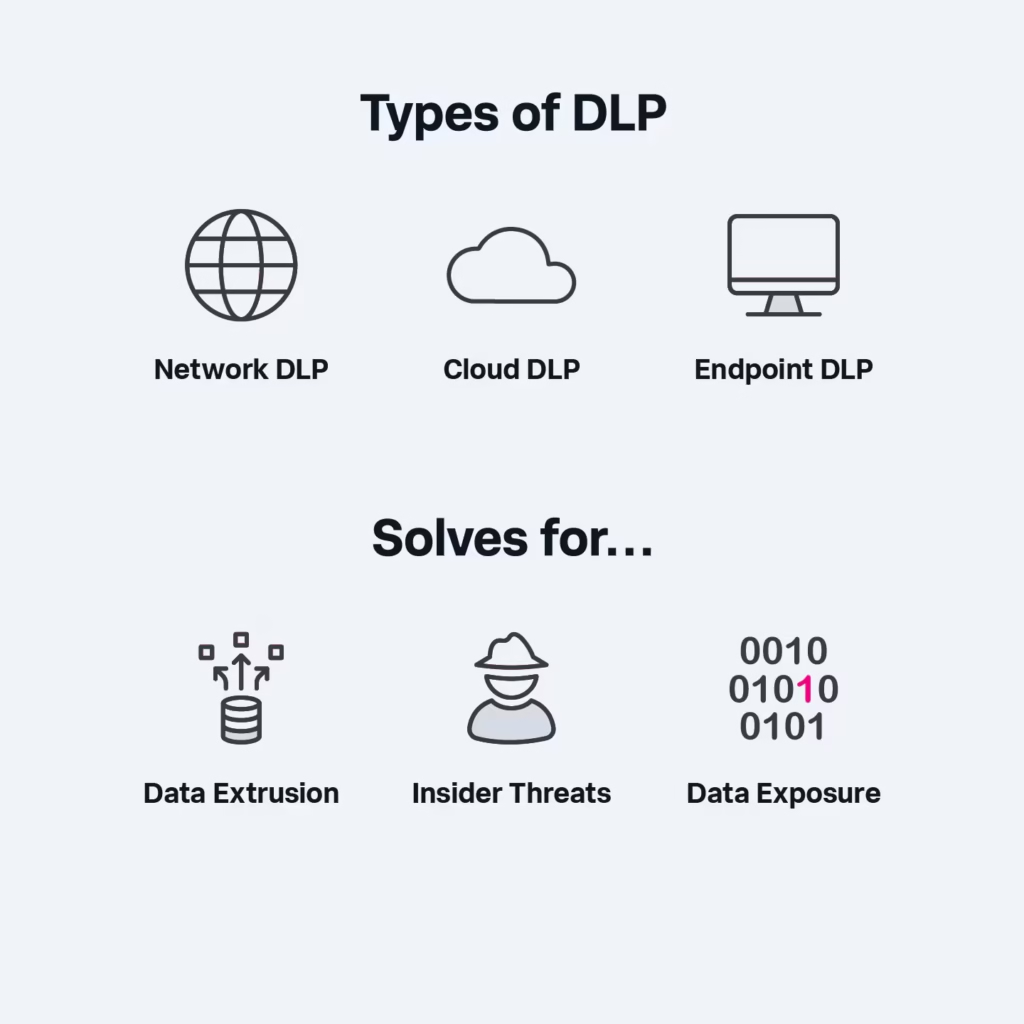
To implement the best plan for data loss prevention, organizations must adopt a multi-layered strategy that integrates different data loss prevention methods. A DLP project plan should include technical solutions, procedural safeguards, and user education to prevent unauthorized access, loss, or leakage of sensitive data.
Key Data Loss Prevention Methods
- Content Discovery & Data Classification
- Identify where sensitive data is stored (on-premises, cloud, endpoints).
- Use automated data discovery tools to classify data based on sensitivity levels.
- Implement labeling policies (e.g., public, internal, confidential, highly restricted).
- Encryption & Access Controls
- Encrypt data at rest, in motion, and in use to prevent unauthorized access.
- Enforce role-based access control (RBAC) and multi-factor authentication (MFA).
- Restrict USB access, file transfers, and external email sharing for sensitive data.
- Endpoint Protection & Monitoring
- Deploy endpoint DLP solutions to monitor and prevent data leaks.
- Control copy-paste functions, screen captures, and unauthorized file transfers.
- Detect suspicious insider activity with user behavior analytics (UBA).
- Network Security & Traffic Filtering
- Implement firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
- Use data-in-motion DLP solutions to monitor outgoing traffic for unauthorized data transfers.
- Block access to unapproved cloud storage and external email services.
- Cloud Security & SaaS Protection
- Use CASB (Cloud Access Security Broker) solutions to monitor cloud data movements.
- Implement zero-trust architecture for secure access control.
- Restrict shadow IT usage by monitoring unsanctioned applications.
- Incident Response & Data Backup
- Develop a DLP incident response plan to quickly contain breaches.
- Schedule regular backups to ensure business continuity in case of a ransomware attack.
- Implement real-time alerting and automated responses for suspected data leaks.
DLP Implementation Checklist: Key Steps for Success

To ensure a smooth DLP implementation project plan, organizations must follow a structured approach that includes policy creation, technology deployment, and user training. This DLP implementation checklist outlines the essential steps needed for a successful data loss prevention strategy.
Step 1: Identify & Classify Critical Data
- Conduct a data inventory to locate sensitive information (customer records, financial data, intellectual property).
- Classify data based on sensitivity levels (public, internal, confidential, restricted).
- Determine where data resides (on-premises servers, cloud, endpoints, databases).
Step 2: Assess Risks & Compliance Requirements
- Conduct a risk assessment to identify potential data leakage points.
- Align DLP policies with industry regulations such as GDPR, HIPAA, PCI DSS, and CCPA.
- Define acceptable use policies (AUP) for data access, sharing, and storage.
Step 3: Select the Right DLP Solutions
- Evaluate DLP vendors based on scalability, integration, and compliance needs.
- Choose on-premises, cloud-based, or hybrid DLP solutions based on business infrastructure.
- Ensure integration with SIEM (Security Information and Event Management), firewalls, and access controls.
Step 4: Define & Enforce DLP Policies
- Develop DLP rules for data access, transfer, and storage.
- Configure automated alerts and blocking mechanisms for unauthorized data movements.
- Set up role-based access controls (RBAC) to limit data exposure.
Step 5: Deploy in Phases (Crawl, Walk, Run Approach)
- Start with a pilot program to test DLP policies on a small dataset.
- Gradually expand deployment to critical departments and high-risk areas.
- Continuously refine policies based on real-world scenarios and audit findings.
Step 6: Train Employees & Raise Awareness
- Conduct regular cybersecurity awareness training on DLP best practices.
- Educate employees on phishing threats, insider risks, and safe data handling.
- Implement policy reminders and security pop-ups for data-sharing activities.
Step 7: Monitor, Audit, & Optimize
- Use real-time monitoring tools to track data access, movement, and anomalies.
- Conduct regular security audits to assess the effectiveness of DLP measures.
- Continuously update policies based on new threats and compliance changes.
Following this DLP implementation checklist helps organizations create a structured approach to securing sensitive data, reducing data breaches, and ensuring regulatory compliance.
MORE: Top 10+ Cybersecurity Threats: Prevention and Mitigation Strategies
DLP Implementation Project Plan: How to Execute a Successful Rollout

A well-structured DLP implementation project plan is essential for organizations looking to prevent data breaches, insider threats, and compliance violations. Implementing data loss prevention is not just about installing software, it requires a phased approach to policy development, risk assessment, technology deployment, and continuous monitoring.
Below is a step-by-step DLP project plan to ensure a successful implementation:
Phase 1: Discovery & Risk Assessment
- Conduct a data discovery process to identify where sensitive data resides (on-premises, cloud, endpoints).
- Assess potential vulnerabilities in existing security controls, user access, and data transfer methods.
- Map DLP requirements to regulatory frameworks (GDPR, HIPAA, PCI DSS).
Phase 2: Define Policies & Compliance Measures
- Establish a DLP governance framework with stakeholders from IT, legal, compliance, and business units.
- Develop clear policies on data classification, access control, and incident response.
- Define acceptable usage policies (AUP) for email, cloud storage, removable media, and file transfers.
Phase 3: Proof of Concept (Pilot Testing)
- Test DLP solutions in a controlled environment before full deployment.
- Deploy data classification and monitoring policies to assess effectiveness and false positives.
- Validate integration with SIEM, access control systems, and cloud security tools.
Phase 4: Full Deployment & Enforcement
- Implement DLP policies across all business units and IT environments.
- Enable automated alerts, policy tips, and blocking mechanisms for unauthorized data movement.
- Establish a 24/7 monitoring system for real-time threat detection and incident response.
Phase 5: Training, Monitoring, & Continuous Improvement
- Conduct regular cybersecurity training for employees on safe data handling and insider threat awareness.
- Perform ongoing audits to refine DLP policies and address emerging threats.
- Update policies based on regulatory changes, new technologies, and evolving business needs.
READ: What Does Defensive and Offensive Methodologies Mean?
Secure Design Strategies for Data Loss Prevention

A DLP project plan should incorporate secure design strategies to minimize data leakage, strengthen cybersecurity, and ensure compliance. These strategies focus on structuring security from the ground up, making data protection an integral part of IT and business operations rather than an afterthought.
1. Zero Trust Security Model
- Implement a Zero Trust framework, ensuring least privilege access for employees and vendors.
- Require multi-factor authentication (MFA) for accessing sensitive data.
- Use context-aware access controls, allowing access based on location, device, and user behavior.
2. Data Masking & Tokenization
- Use data masking techniques to obscure sensitive data when shared with third parties.
- Implement tokenization to replace sensitive data with non-sensitive placeholders, reducing exposure risk.
- Apply role-based viewing permissions to limit who can see confidential information.
3. Cloud Security Best Practices
- Enforce cloud DLP policies to prevent unauthorized sharing of files via Google Drive, OneDrive, Dropbox, and AWS.
- Use Cloud Access Security Brokers (CASB) to monitor and control data flow in cloud environments.
- Encrypt data stored in public, private, or hybrid clouds to prevent unauthorized access.
4. Endpoint & Application Security
- Restrict removable storage usage (USB, external hard drives) for employees handling sensitive data.
- Secure corporate laptops, desktops, and mobile devices with endpoint DLP solutions.
- Monitor file uploads, downloads, and transfers across business applications.
5. Integration with Threat Intelligence & SIEM
- Integrate DLP with Security Information and Event Management (SIEM) solutions for real-time monitoring.
- Use AI-driven analytics to detect anomalous behavior and prevent insider threats.
- Automate incident response workflows to contain breaches before they escalate.
ALSO SEE: OPNsense Zenarmor Vs Suricata: A Comprehensive Review
Common Challenges in DLP Implementation & How to Overcome Them

While implementing a DLP project plan, organizations often encounter technical, operational, and cultural challenges that can hinder data protection efforts. To ensure a successful data loss prevention strategy, businesses must anticipate these challenges and develop proactive solutions.
1. Lack of Stakeholder Buy-In
Challenge:
- Executives and employees may resist DLP implementation, viewing it as a disruptive or unnecessary investment.
- Lack of support from legal, compliance, and IT teams can delay or weaken the enforcement of DLP policies.
Solution:
- Educate stakeholders on the importance of DLP in cybersecurity, emphasizing compliance and financial risks.
- Conduct cost-benefit analysis to demonstrate ROI and long-term value.
- Involve C-level executives, IT leaders, and compliance officers early in the process.
2. High False Positives & Policy Overload
Challenge:
- Overly restrictive DLP policies can generate excessive false positives, causing frustration among employees.
- A rigid DLP implementation can lead to operational slowdowns and disrupt legitimate business workflows.
Solution:
- Adopt a crawl, walk, run approach; start with limited policies and gradually scale up.
- Use machine learning and AI-driven DLP tools to reduce false alerts and improve accuracy.
- Fine-tune DLP rules based on real-world testing and user feedback.
3. Balancing Security with Productivity
Challenge:
- Strict data protection policies may hinder productivity, making collaboration difficult.
- Employees may circumvent security controls by using unauthorized cloud apps or personal email.
Solution:
- Implement flexible policies that balance security with usability.
- Allow conditional access controls, where certain users or departments can have approved exceptions.
- Use security awareness programs to train employees on safe data handling.
4. Insider Threats & Data Exfiltration
Challenge:
- Employees, contractors, or former staff may intentionally or unintentionally leak sensitive data.
- Traditional cybersecurity measures focus on external threats, while insider threats remain undetected.
Solution:
- Deploy user behavior analytics (UBA) to monitor suspicious activity and detect anomalies.
- Implement role-based access control (RBAC) to limit access to sensitive information.
- Use DLP policies to prevent unauthorized file transfers, email forwarding, and USB data copying.
5. Managing Regulatory Compliance
Challenge:
- Organizations handling personal, financial, or healthcare data must comply with GDPR, HIPAA, PCI DSS, and CCPA.
- Failing to meet compliance requirements can result in legal fines and reputational damage.
Solution:
- Align DLP implementation checklists with compliance frameworks to ensure audit readiness.
- Automate data discovery and classification to identify and protect sensitive information.
- Regularly update DLP policies to reflect new regulatory changes and industry standards.
READ MORE: Dual Firewall vs Single Firewall DMZ: A Comprehensive Analysis
Conclusion
The best plan for data loss prevention is one that integrates proactive security measures, compliance alignment, and user awareness into a holistic cybersecurity framework.
Organizations must recognize that DLP is not just a tool but a strategic approach to safeguarding sensitive information, preventing breaches, and maintaining regulatory compliance.
By following the DLP implementation checklist and addressing common challenges, organizations can establish a future-proof data protection framework that not only prevents data breaches but also enhances business resilience in an increasingly cyber-threatened world.
Data is the lifeblood of modern enterprises, and protecting it should be a top priority. Implementing the best plan for data loss prevention in cybersecurity requires the right combination of technology, governance, and user awareness.
Organizations that invest in a well-planned DLP project will significantly reduce risks, protect brand reputation, and maintain regulatory compliance in the long run.
FAQ
What is the plan for data loss prevention?
A data loss prevention (DLP) plan is a structured strategy that organizations implement to prevent unauthorized access, leakage, or theft of sensitive data. It involves:
Identifying & classifying sensitive data (e.g., customer records, financial data, intellectual property).
Defining security policies for data access, sharing, and storage across endpoints, networks, and the cloud.
Implementing DLP technologies to monitor, detect, and block unauthorized data movements.
Training employees on safe data handling and insider threat prevention.
Regularly auditing and updating DLP policies to align with evolving threats and compliance regulations.
A well-executed DLP implementation project plan ensures that critical business data remains protected against both external cyberattacks and insider threats.
What is the best way to protect data from loss?
The best way to protect data from loss is through a multi-layered security approach that includes:
Data Classification & Risk Assessment – Identifying and labeling sensitive information based on importance.
Encryption & Access Controls – Encrypting data at rest, in motion, and in use, and enforcing role-based access control (RBAC).
Endpoint & Cloud Security – Deploying DLP solutions to monitor USB drives, emails, file transfers, and cloud storage.
Network Security & Monitoring – Using firewalls, SIEM tools, and intrusion detection systems (IDS/IPS) to prevent data breaches.
Regular Backups & Disaster Recovery – Creating automated backups and incident response plans to restore lost data.
Employee Training & Insider Threat Detection – Educating employees on cyber threats and security policies while monitoring for anomalous activities.
Combining these data loss prevention methods ensures continuous data protection while maintaining business continuity.
What are the best practices for DLP?
To implement a strong data loss prevention strategy, organizations should follow these best practices:
Identify and Classify Sensitive Data – Conduct data discovery to locate and categorize critical information.
Define and Enforce DLP Policies – Establish clear rules for data handling, sharing, and storage.
Implement Encryption & Access Controls – Protect sensitive files with encryption and enforce least privilege access.
Monitor and Detect Data Movement – Deploy DLP software to track how data moves across networks and devices.
Train Employees & Raise Awareness – Conduct regular cybersecurity training to prevent accidental data leaks.
Regularly Audit and Update DLP Strategies – Continuously test and refine DLP policies based on security trends and compliance changes.
Develop an Incident Response Plan – Ensure quick containment and recovery in case of a data breach or accidental exposure.
Following these DLP best practices helps organizations reduce data loss risks, improve regulatory compliance, and strengthen cybersecurity defenses.
What are the 5 steps to successfully implement data loss prevention?
A DLP implementation project plan should follow these five key steps:
Data Discovery & Risk Assessment Identify sensitive data locations (on-premises, cloud, endpoints).
Analyze potential risks and compliance requirements (GDPR, HIPAA, PCI DSS).
Define DLP Policies & Compliance Framework Establish rules for data access, sharing, and protection.
Align policies with industry regulations and internal security protocols.
Select & Deploy the Right DLP Solutions Implement network, endpoint, and cloud-based DLP tools.
Integrate SIEM, threat intelligence, and access control solutions.
Employee Training & Insider Threat Prevention Conduct cybersecurity awareness programs to educate employees.
Implement user behavior analytics (UBA) to detect suspicious activities.
Continuous Monitoring, Auditing & Optimization Set up real-time alerts for unauthorized data transfers.
Regularly audit and fine-tune DLP policies to improve efficiency.
If you’re ready to take the next step in your cybersecurity journey? You can do that with an expert beside you to guide you through without having to stress much. Schedule a one-on-one consultation with Tolulope Michael, a cybersecurity professional with over a decade of field experience. This will allow you to gain personalized insights and guidance tailored to your career goals.
Visit tolumichael.com now to book your session. This is your opportunity to embark on your cybersecurity career with confidence. Don’t miss out!

